- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Show search value with timechart
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I show search value with timechart?
Dear professionals,
I have a search string like this
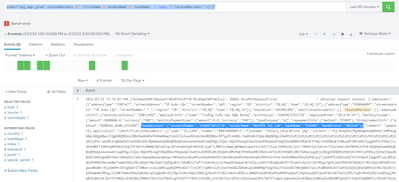
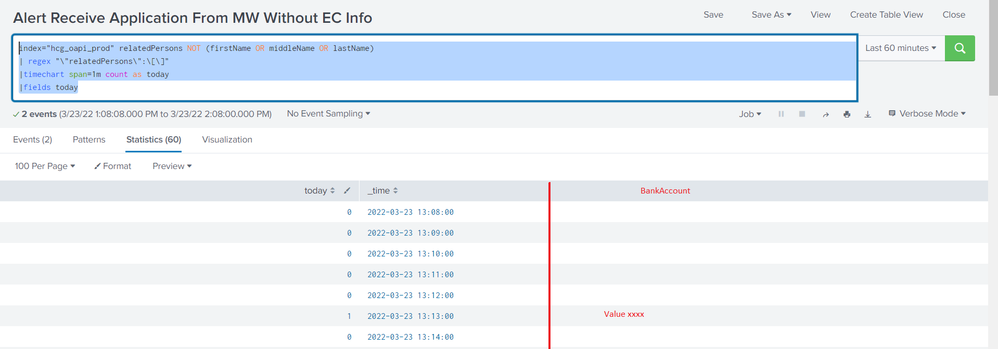
index="hcg_oapi_prod" relatedPersons NOT (firstName OR middleName OR lastName) | regex "\"relatedPersons\":\[\]"And this is the result. The results have "bankAccount" value.
Then I add timechart like this
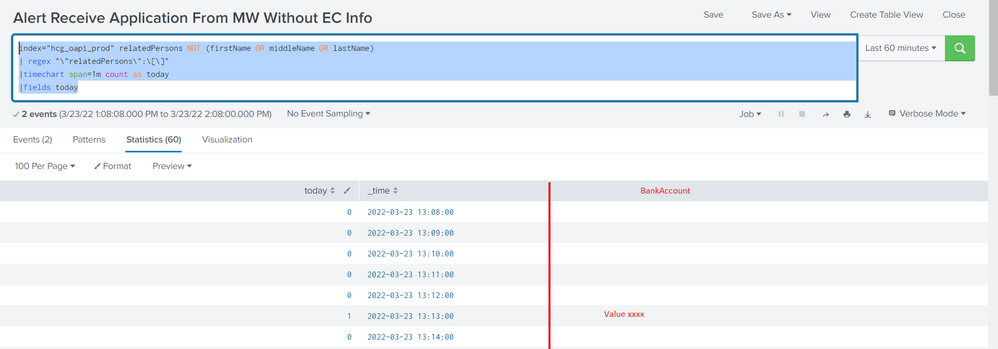
index="hcg_oapi_prod" relatedPersons NOT (firstName OR middleName OR lastName)
| regex "\"relatedPersons\":\[\]"
|timechart span=1m count as today
|fields todayHow can I add a column for bankAccount when today = 1?
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) i think the regex is not needed as you filter that on first line itself.
2) timechart requires a "BY" clause i think.
Please check this one:
index="hcg_oapi_prod" relatedPersons NOT (firstName OR middleName OR lastName)
|timechart span=1m count as today BY host
|fields today- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @lamnguyentt1,
there's something not clear for me in your search: why do you extract "relatedPersons" field if you don't use in timechart?
Rememeber that after a transaction command (as stats or timechart), you have only the fields in the command, in your case only _time and count renamed in today.
If you want more fields you have to put them in the command, e.g.:
index="hcg_oapi_prod" relatedPersons NOT (firstName OR middleName OR lastName)
| timechart span=1m count as today BY bankAccountIf you want more fields (e.g. relatedPersons), you have to use bin and stats, something like this:
index="hcg_oapi_prod" relatedPersons NOT (firstName OR middleName OR lastName)
| regex "\"relatedPersons\":\[\]"
| bin span=1m _time
| stats values(relatedPersons) AS relatedPersons count as today BY bankAccountCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Mr. @gcusello
For clearly,
The origin search is
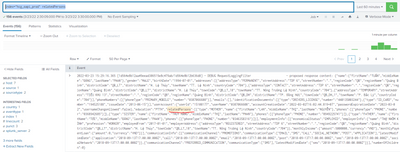
index="hcg_oapi_prod" relatedPersons
And this is results
I want to create the alert when it matches this condition
1. The results have "relatedPersons":[] and don't have (firstName OR middleName OR lastName)
2. I will count the search result each 1 minute if count >1, I will send an email and I want to attach "bankAccount value (for other person easy to search when they receive the email)
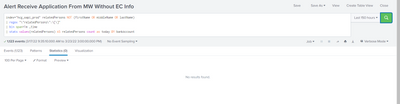
I have use your search string but it shows that
Please help me, print result like this