- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I filter all events to exclude this string...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I filter all events to exclude this string?
Hi,
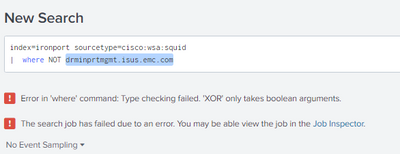
I have an index of log events and I have been asked to exclude all events with a certain string in it. The String I need to omit is drminprtmgmt.isus.emc.com. This string (which represents a device) is not mapped to any field currently. How can I filter all events to exclude this string?
This is currently what I have (which does NOT work):
Many thanks,
Patrick
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @POR160893,
as @PickleRick said, you have to use the search command or (better) put the string to exclude in the main search, something like this:
index=ironport sourcetype=cisco:wsa:squid NOT drminprtmgmt.isus.emc.comCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked perfectly, thanks! 😁
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @POR160893 ,
good for you, if this answer solves your need, please accept it or the other people of Community, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't use the "where" command - it's meant for boolean-evaluating conditions. Use the "search" command.