- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I change the order of the fields in my pie...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
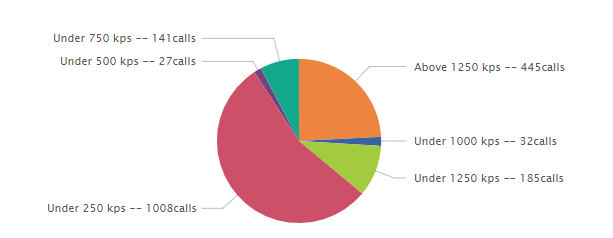
I have the following search:
....| eval "cs"=case(CallRate<=250,"Under 250 kps", CallRate<=500,"Under 500 kps", CallRate<=750,"Under 750 kps", CallRate<=1000,"Under 1000 kps", CallRate<=1250,"Under 1250 kps", CallRate>1250, "Above 1250 kps") | stats count by cs | eval cs=cs+" -- "+count + "calls"
I want to make the piechart easy for my client to understand but the fields in the piechart organize themselves alphabetically. Is there a way I could sort them by the original way like above? The following is the result piechart:
I want it to be in this order:
Under 250 kps, Under 500 kps, Under 750 kps, Under 1000 kps, Under1250 kps, Above 1250 kps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| eval "cs"=case(CallRate<=250,"1.Under 250kps", CallRate<=500,"2.Under 500kps", CallRate<=750,"3.Under 750kps", CallRate<=1000,"4.Under 1000kps", CallRate<=1250,"5.Under 1250kps", CallRate>1250, "6.Above 1250kps") | stats count by cs| eval "cs"=replace('cs',"^(\d{1}).","")
| eval cs=cs+" -- "+count + "calls"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| eval "cs"=case(CallRate<=250,"1.Under 250kps", CallRate<=500,"2.Under 500kps", CallRate<=750,"3.Under 750kps", CallRate<=1000,"4.Under 1000kps", CallRate<=1250,"5.Under 1250kps", CallRate>1250, "6.Above 1250kps") | stats count by cs| eval "cs"=replace('cs',"^(\d{1}).","")
| eval cs=cs+" -- "+count + "calls"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your problem is resolved, please accept an answer (even if it's your own).
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tamduong16, sequence them in your case() function so that they get automatically sorted. Try the following:
| eval "cs"=case(CallRate<=250,"1. Under 250 kps", CallRate<=500,"2. Under 500 kps", CallRate<=750,"3. Under 750 kps", CallRate<=1000,"4. Under 1000 kps", CallRate<=1250,"5. Under 1250 kps", CallRate>1250, "6. Above 1250 kps")
| stats count by cs
| eval cs=cs+" -- "+count + "calls"
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the idea. It works but give me unwanted numeric at the beginning which I could write another eval expression to resolve that and work perfect. Here is the eval expression I added in.
| eval "cs"=case(CallRate<=250,"1.Under 250kps", CallRate<=500,"2.Under 500kps", CallRate<=750,"3.Under 750kps", CallRate<=1000,"4.Under 1000kps", CallRate<=1250,"5.Under 1250kps", CallRate>1250, "6.Above 1250kps") | stats count by cs| eval "cs"=replace('cs',"^(\d{1}).","")
| eval cs=cs+" -- "+count + "calls"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can force an order by adding a numeric field to sort against. See this example.
... | eval "cs"=case(CallRate<=250,"Under 250 kps", CallRate<=500,"Under 500 kps", CallRate<=750,"Under 750 kps", CallRate<=1000,"Under 1000 kps", CallRate<=1250,"Under 1250 kps", CallRate>1250, "Above 1250 kps") | eval sortOrder=case(CallRate<=250,1, CallRate<=500,2, CallRate<=750,3, CallRate<=1000,4, CallRate<=1250,5, CallRate>1250, 6) | stats count values(sortOrder) as sortOrder by cs | eval cs=cs+" -- "+count + "calls" | sort sortOrder
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this doesn't work 😞
The fields in the piechart don't get sort and in addition it make everything harder to read.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm... It works on my laptop under Splunk 6.6.2.
If this reply helps you, Karma would be appreciated.