- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Help with query to notify when data ingestion is s...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
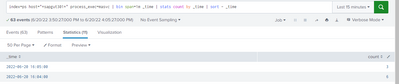
Query to find when host is stopped,
Here as mentioned in picture, the field _time stopped at the time , when the host is stopped and it's back to normal, when host is started . So need to trigger alert when host is stopped.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @smanojkumar,
the query is the same, the thing to change are the Time Frame and the scheduling.
Anyway, I hint to use an high frequency (e.g. 5 minutes) because if you don't receive logs you're blind!
The minimum frequency depends on eventual delays you have in your data ingestion.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Thanks for your response.
If in case , we should trigger only it does not brings data for 1 hour, What will the query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @smanojkumar,
the query is the same, the thing to change are the Time Frame and the scheduling.
Anyway, I hint to use an high frequency (e.g. 5 minutes) because if you don't receive logs you're blind!
The minimum frequency depends on eventual delays you have in your data ingestion.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @smanojkumar,
my hint is to create a simple alert like the following:
| metasearch index=ps host="*sapgut301*" process_exec=masvc | head 1scheduling it every 5 minuts, triggered if results=0.
It's a very quick search that you can run also with an higher frequency.
If instead you want to know if there's one host missing, it's a little bit different, because you need to have a list of host to monitor and put them in a lookup (called e.g. perimeter.csv) containing at least one column (called host) and scheduling a search like the following e.g. every 5 minutes:
| metasearch index=ps host="*sapgut301*" process_exec=masvc
| eval host=lower(host)
| stats count BY host
| append [ | inputlookup perimeter.csv | eval host=lower(host), count=0 | fields host count ]
| stats sum(count) AS total BY host
| where total=0Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
It's worked, Thanks.