- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Get the chart count by in the form of percenta...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey folks,
I am trying to pull a result based on chart count by, I am also not sure if there is any other command which can fulfil this result.
So the end result what I am looking for is :
http.status IN (200,400,403) | chart count by path http.status
path. 200. 400 403
/abc 10% 30% 60%
/xyz 20% 40% 40%
/home 35% 35% 30%
I have checked the community answers but none of them is close to what I am looking for.
if someone could just guide and help me through this, that would be really helpful.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to the other great answers here. Here's a simplified/more flexible/dynamic way of doing it:
(base search) http.status IN (200,400,403)
| eval status="status_".'http.status'
| chart count by path status
| addtotals
| foreach status_* [| eval "<<FIELD>>%"=tostring(round(<<FIELD>>/Total*100,2))+"%"]
| table path *%
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to the other great answers here. Here's a simplified/more flexible/dynamic way of doing it:
(base search) http.status IN (200,400,403)
| eval status="status_".'http.status'
| chart count by path status
| addtotals
| foreach status_* [| eval "<<FIELD>>%"=tostring(round(<<FIELD>>/Total*100,2))+"%"]
| table path *%
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you so much. it worked perfectly.
just one thing : wht is this line doing,
eval status="status_".'http.status'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kamlesh_vaghela can you please help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Gr0und_Z3r0 I didn't get this part at all, not sure what is this. I don't have these values at all.
| eval http_200 = case(count=1, 2500, count=2, 3904, count=3, 3156, count=4, 40566) | eval http_400 = case(count=1, 250, count=2, 32, count=3, 101, count=4, 50) | eval http_403 = case(count=1, 22, count=2, 390, count=3, 310, count=4, 400) | eval path = case(count=1, "Path_A", count=2, "Path_B",count=3, "Path_C",count=4, "Path_D")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That part is me creating a test data for my query. You can ignore it. For you it will be the main search that will derive your paths and response codes. Post which you can use the foreach operations to derive the percentage table.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
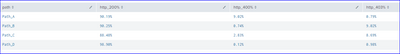
Hi @bijodev1 ,
Try this way of using foreach function for the result table.
| makeresults count=4
| streamstats count
| eval http_200 = case(count=1, 2500, count=2, 3904, count=3, 3156, count=4, 40566)
| eval http_400 = case(count=1, 250, count=2, 32, count=3, 101, count=4, 50)
| eval http_403 = case(count=1, 22, count=2, 390, count=3, 310, count=4, 400)
| eval path = case(count=1, "Path_A", count=2, "Path_B",count=3, "Path_C",count=4, "Path_D")
| fields - count
| addtotals
| table path http_200 http_400 http_403 Total
| foreach http_200
[ eval http_200%= tostring(round(<<FIELD>>/Total*100,2))+"%"]
| foreach http_400
[ eval http_400%= tostring(round(<<FIELD>>/Total*100,2))+"%"]
| foreach http_403
[ eval http_403%= tostring(round(<<FIELD>>/Total*100,2))+"%"]
| table path http_200% http_400% http_403%
Please do upvote if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
foreach doesn't make sense in this instance as you are only listing one field in each foreach command - replace with this
| eval http_200%= tostring(round(http_200/Total*100,2))+"%"
| eval http_400%= tostring(round(http_400/Total*100,2))+"%"
| eval http_403%= tostring(round(http_403 /Total*100,2))+"%"