- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Field search needs unnecessary wildcard character ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Field search needs unnecessary wildcard character *
I am doing search on data coming from fluentd k8s.
On top of that data , I wanted to filter on basis of field.
Add to search field prompts that, there would be count of 7 events. But surprisingly its Zero.
So I did some trial and error to put wildcards to get data. Here it is.
index=main 200 namespace="*app-s*pace*"
Now all the & events shows up !!
My Question is Why is this happening?
And why -s*pace.
In some fields, keeping * also does not give accurate events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this a regex based field extraction?
Have a look at the article below and see if this is what you're running into.
https://www.splunk.com/blog/2011/10/07/cannot-search-based-on-an-extracted-field.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
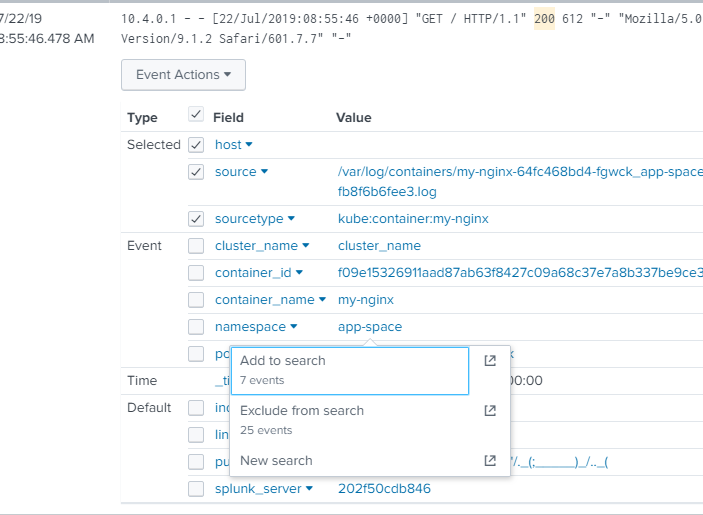
I had no intention to do namespace="*app-s*pace*" as the result did not show on app-space . I did this trial and error and added these * around the string.
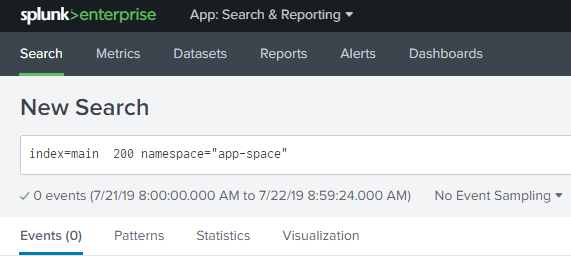
If you see the 1st image, the field is a plain string. app-space and also suggest 7 events will appear but clicking on it (2nd image). Zero events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I believe understand what the problem is. you're describing something similar to what the blog post I shared describes.
The solution for the problem in the article is to add the below stanza to your fields.conf. But that depends on whether it was a regex based field extraction or not, which was my question to you.
[namespace]
INDEXED_VALUE = false
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a similar problem.
Running the suggested test below still give me no result. So this blog is unrelated.
"search sourcetype=MyEvents MyField=* | search MyField=ValidValue"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Honestly, This is my 5th day with Splunk. I have not extracted any fields myself. I set up fluentd in my k8s cluster . Created a HEC in my splunk and provided that data to fluentd running on my k8s. That's it.
Then I can see these data with fields populated in my splunk.(my splunk is a docker container)
let me try as you suggested (blog post).