- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Eliminate Specific results from search query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
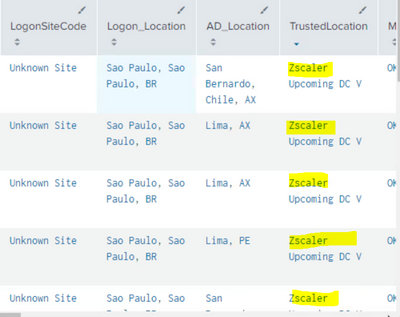
I want to eliminate TruestedLocation = Zscaler in my splunk search result.
Below is my query and screenshot. Please help me with splunk query.
Thanks in advance.
index=test "vendorInformation.provider"=IPC
| eval Event_Date=mvindex('eventDateTime',0)
| eval UPN=mvindex('userStates{}.userPrincipalName',0)
| eval Logon_Location=mvindex('userStates{}.logonLocation',0)
| eval Event_Title=mvindex('title',0)
| eval Event_Severity=mvindex('severity',0)
| eval AAD_Acct=mvindex('userStates{}.aadUserId',0)
| eval LogonIP=mvindex('userStates{}.logonIp',0)
| eval Investigate=+"https://portal.azure.com/#blade/Microsoft_AAD_Acct
| stats count by Event_Date, Event_Title, Event_Severity UPN Logon_Location LogonIP Investigate
| lookup WeirMFAStatusLookup.csv userPrincipalName as UPN
| lookup Lookup_EMPADInfo.csv userPrincipalName as UPN
| lookup WeirSiteCode2IP.csv public_ip as LogonIP
| lookup ZscalerIP CIDR_IP as LogonIP
| lookup WeirTrustedIPs.csv TrustedIP as LogonIP
| fillnull value="Unknown Site" site_code
| eval AD_Location=st + ", " + c
| fillnull value="OK" MFAStatus
| eval TrustedLocation=if(isnull(TrustedLocation), ZLocation, TrustedLocation)
| rename site_code as LogonSiteCode
| table Event_Date, Event_Title, Event_Severity UPN LogonIP LogonSiteCode Logon_Location AD_Location TrustedLocation MFAStatus count Investigate
| sort - Event_Date
@isoutamo @saravanan90 @thambisetty @ITWhisperer @gcusello @to4kawa
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are saying you want to remove the field value 'Zscaler' from the TrustedLocation field, where Zscaler is one value of a multi-value field, then this will remove it
| eval TrustedLocation=mvfilter(!match(TrustedLocation,"Zscaler"))If I've misunderstood your requirement and you want to remove all rows where TrustedLocation contains Zscaler then
| where isnull(mvfind(TrustedLocation,"Zscaler"))Hope this helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
eliminate?
...
| where !match(TruestedLocation,"Zscaler")or
...
| rex field=TruestedLocation mode=sed "s/Zscaler//"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are saying you want to remove the field value 'Zscaler' from the TrustedLocation field, where Zscaler is one value of a multi-value field, then this will remove it
| eval TrustedLocation=mvfilter(!match(TrustedLocation,"Zscaler"))If I've misunderstood your requirement and you want to remove all rows where TrustedLocation contains Zscaler then
| where isnull(mvfind(TrustedLocation,"Zscaler"))Hope this helps