- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Concat 2 or more search queries into single ta...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Concat 2 or more search queries into single table
Hello, I am a freshmen with splunk.
I got a problem trying to concat two/more searches into 1.
pretty much my data looks like so
{
"TimeStamp": "\/Date(1630425120000)\/",
"Name": "Plan-MemoryPercentage-Maximum.json",
"Maximum": 14
}
{
"TimeStamp": "\/Date(1630425120000)\/",
"Name": "Plan-MemoryPercentage-Average.json",
"Average": 14
}
both sets will have the same timeStamp for the entries and I just want a table that will have the matching time stamps and a column for max and a column for avg
so far I'm able to get a single table going that has a query that looks like
Name="Plan-MemoryPercentage-Maximum.json" | table * | fields TimeStamp, Maximum | fields - _time, _raw
but I'm really struggling to figure out how to concat 2 searches into 1 table anyone have any ideas?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rite10privacy10 ,
Please try this:
index="mine" (sourcetype="Plan-MPercentage-Maximum.json" OR sourcetype="Plan-MPercentage-Average.json")
| stats values(TimeStamp) as Timestamp, values(Average) as Average, values(Maximum) as Maximum
Let me know if this helps.
Thanks,
S
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this is wat the query you wanted me to try looks like as a result.
Edit: the thing is that know there is a value tied to each date so I'm not sure why some of the entries show nothing?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
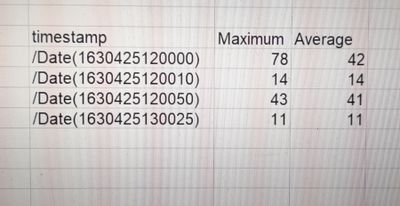
I think I misinterpreted the output that you'd like to see from your query. Please correct me if I'm wrong, but are you expecting an output like this (I've filled the fields randomly as of now, but if you can show as to how you visualise the output when a few rows of the data, that would be great)?
Once you confirm the desired output that you'd like to see, we can built the query accordingly.
Thanks,
S
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Understood now. Please try something like this (May contain typos, so please edit the name of the fields as they are in your data):
index="mine" (sourcetype="Plan-MPercentage-Maximum.json" OR sourcetype="Plan-MPercentage-Average.json")
| stats values(sourcetype) as sourcetype, dc(sourcetype) as dcount, values(Maximum) as Maximum, values(Average) as Average by Timestamp
| where dcount = 2
| fields - sourcetype dcount
Thank you,
Shivanshu
***If this helped, please accept it as a solution. It helps others to find the solution for similar issues quickly.***
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry was not able to get that working still working on it took a break for a few days from it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes that's exactly what im looking for actually XD.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @rite10privacy10 ,
If the data is stored in the same index and sourcetype, please try something like this:
index=foo sourcetype=bar
| stats values(Maximum) as Maximum, values(Average) as Average, values(Timestamp) as timestamp by Name
If both sets of data are in the same Index, but different sourcetype, then:
index=foo (sourcetype=bar OR sourcetype=baz)
| stats values(Maximum) as Maximum, values(Average) as Average, values(Timestamp) as timestamp by Name
If you can share an image of the how you'd like to see rhe output, I can help you to refine the query more per your expectations.
Hope this helps.
Thanks,
S
***If this helped, please accept it as a solution. It helps others to find the solution for similar issues quickly.***
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
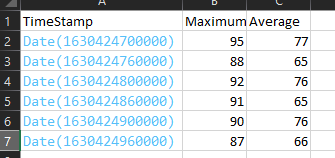
That didnt quiet work for me. it was missing values somehow.
so like i got this
```
index="mine" (sourcetype="Plan-MPercentage-Maximum.json" OR sourcetype="Plan-MPercentage-Average.json")| table * | fields TimeStamp, Average, Maximum | fields - _time, _raw
```
and it looks like this
because those timestamps are the same i want them to share a row not have individual rows
edit * there would also be the chance i have to throw a minimum in there aswell.*
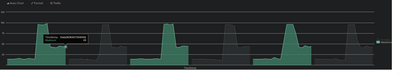
Edit: when i go into the visualization tab i see this
were as i feel like if i had the maximum and average on the same row per unique date the graphs would be overlapping instead