- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Can you use an if statement for the value of t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you use an if statement for the value of two different fields?
Hello,
I'm a bit new to Splunk, so I'm still learning.
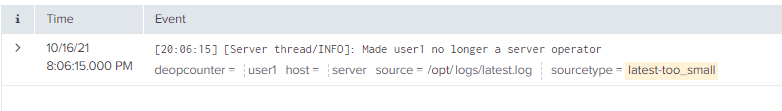
I have created two fields, an opscounter, and a deopcounter. The opscounter keeps count of how many times the field's value, or in this case, the value equates to a username is promoted to admin. If a user is promoted to admin, their count goes up on the opscounter; however, if they are demoted, the deopscounter goes up as well. As you can see in the opscounter image below, user1 was made an admin, and in the opscounter the count of 1, but in the deopscounter, you can see that user1 has a count of one, meaning they were demoted. If they are promoted again, their opscounter value will go to two. If a new user is added, they will automatically be added to the field same if they are demoted, but they will have the same value in both fields. I would like to create a dashboard that displays a list of current admins.
Knowing that is there a way to put every value that is in these fields in an if statement? My thought process is if user1 from opscounter is greater than user1 from deopcounter, display that user. I would like to figure out a way to make this work. If not, I'm open to suggestions on how to get the same results in a dashboard but through a different method.
Any help is appreciated!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
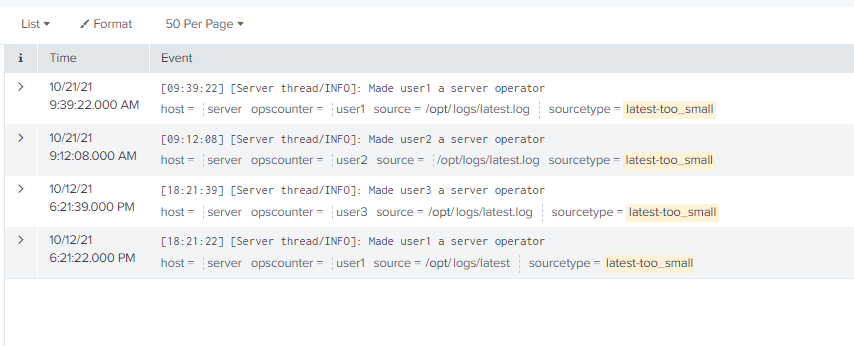
Can you show us sample events, not stats?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, here are some sample events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can do with your fields but it'd be way easier if you had it parsed differently. Why do you parse the same entity (user) into two different fields?
I'd suggest you parse the user separately and the operation ("a server operator" or "no longer a server operator"). Then it'd be very simple.
<your search> | eval opcount=if(operation="a server operator",1,-1)
| stats sum(opcount) by user
| eval finalstate=if(opcount>0,"operator","not operator")
| table user finalstate
Of course there's an assumption that all users start with a "clean slate" which is not necessarily true (you'd get different results depending on your timerange) so it's not a very good idea to calculate the state of your system this way
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can run this example anywhere, but the last two lines will work for your data
| makeresults
| eval _raw="user,C
user1,1
user2,1
user3,1
user1,-1
user1,1"
| multikv forceheader=1
| eval opscounter=if(C=1,1, null()), deopcounter=if(C=-1,1, null())
| table user opscounter deopcounter
| stats sum(opscounter) as Promoted sum(deopcounter) as Demoted by user
| where Promoted-Demoted>0 This will show you all users with Promoted>Demoted, however, note that all users will start with a value of 0 for each, so if a user is already an admin and there are no rows found in your time window it will not show that user
It will handle the case where you only see a demotion, as the score will be <0.
To solve the first case, you will either have to search all time, or save some current state of admins, for example to a lookup file, which is done each night, and then your search could combine the current starting state of admins with the search of promotions/demotions done since that last search.