- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Can you help me with the following regex?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
I want to add a rex field in my search
index="ai-wkst-wineventlog-fr" sourcetype="XmlWinEventLog" source="XmlWinEventLog:Application" (Level=1 OR Level=3) Name="'*'"
I want to extract the text which is included before "ProgID" and after "" and also the text which is after "ProgID"
Outlook a désactivé le ou les compléments suivants :
ProgID : WebExOI.Addin
Could you help me please??
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like this:
(?ms)^(?<message>.*?)\s*:[\r\n\s]+ProgID\s+:\s+(?<ProgID>[^\r\n]+)
See here:
https://regex101.com/r/QdSDvV/1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @jip31
Did any of the answers below solve your problem? If so, please resolve this post by approving the one that helped you. If your problem is still not solved, keep us updated so that someone else can help. Thanks for posting!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello all and many thanks
I want to add this regex in my query
what is the good syntax please?
| rex field=EventData_Xml "(?ms)^(?.?)\s:[\r\n\s]+ProgID\s+:\s+(?[^\r\n]+)f" | table message ProgID
| rex field=EventData_Xml "(?[^\r\n:]+)\s:\s*ProgID\s:\s(?[^\r\n]+)3 | table text1 text2
?????
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This looks like a different question to be asked.
If this reply helps you, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like this:
(?ms)^(?<message>.*?)\s*:[\r\n\s]+ProgID\s+:\s+(?<ProgID>[^\r\n]+)
See here:
https://regex101.com/r/QdSDvV/1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have no result Wen i do this
| rex field=EventData_Xml "(?ms)^(?.?)\s:[\r\n\s]+ProgID\s+:\s+(?[^\r\n]+)f "| table message ProgID
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had an extra trailing f character (now deleted). Try this:
Your Search Here:
| rex field=EventData_Xml "(?ms)^(?<message>.*?)\s*:[\r\n\s]+ProgID\s+:\s+(?<ProgID>[^\r\n]+)"| table message ProgID
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did this work @jip31?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this: (?<text1>[^\r\n:]+)\s:\s*ProgID\s:\s(?<text2>[^\r\n]+)
https://regex101.com/r/fRXqTf/1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello I dont succeed to used it does it something like this :???
rex field=EventData_Xml "(?[^\r\n:]+)\s:\s*ProgID\s:\s(?[^\r\n]+)" | table EventData_Xml
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please make sure to post any code between `? Or format it as a code snippet using the 101010 button in the editor toolbar? Now special characters like <> disappear.
It should be something like:
| rex field=EventData_Xml "(?<message>[^\r\n:]+)\s:\s*ProgID\s:\s(?<ProgID>[^\r\n]+)" | table message ProgID
If that isn't working, then I'd like to see a screenshot, or more extensive piece of sample data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry franck no it doesnt works
you can see the code here
https://cjoint.com/c/HKAjr4hOctc
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you:
- show a screenshot that clearly shows the EventData_Xml field exists and what it look like (feel free to mask any sensitive data)
- test the search in a simple way (so without all the rest of your query), just get the data and apply the rex command.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the screenshot
https://cjoint.com/c/HKAlomr50Rc
no results also in simple way
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Works fine for me: https://imgur.com/a/ew8Io7c
Can you share a screenshot of the search giving no results?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi. Can you provide log samples?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
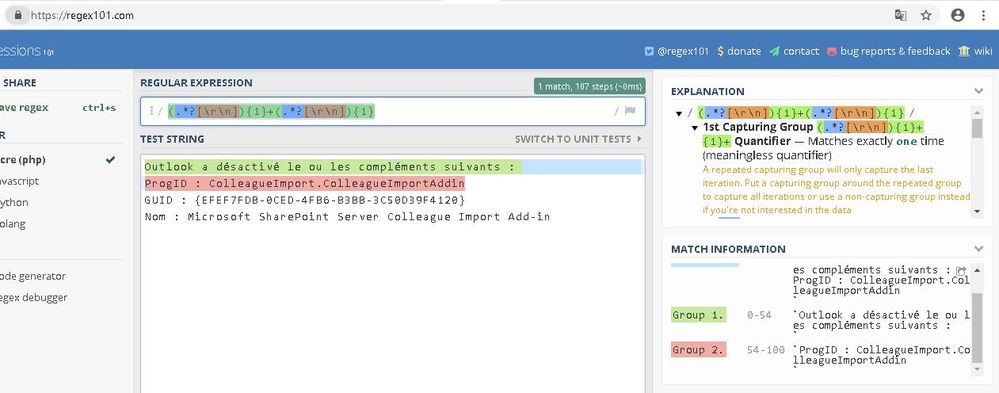
hi
Outlook a désactivé le ou les compléments suivants :
ProgID : ColleagueImport.ColleagueImportAddin
GUID : {EFEF7FDB-0CED-4FB6-B3BB-3C50D39F4120}
Nom : Microsoft SharePoint Server Colleague Import Add-in