- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk SOAR (f.k.a. Phantom)
- :
- Re: Getting error when trying to check if IP is lo...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting error when trying to check if IP is local and make two separate queries to the CrowdStrike app.
Hi everyone,
It might me a silly question 🙂
The simplified case.
3 artifacts within the event with 3 different IP addresses:
- 192.168.0.1
- 192.168.0.2
- 8.8.8.8
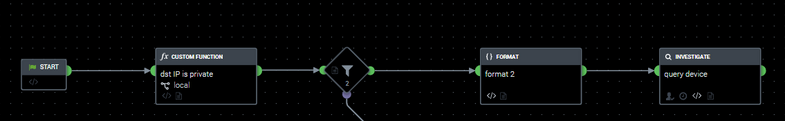
I'm trying to check if IP is local and make separate queries to the crowdstrike (it could be any other app).
Each query should use filter parameter local_ip:"{0}", so I'm using a Format gadget.
I'm getting a error during the execution because "Format" function returns joined value: local_ip:"192.168.0.1, 192.168.0.2". And then it launches crowdstrike app just ones with this filter. But it should be 2 different request with a separate IP address in each one.
I tried to use as a filter parameter for the crowdstrike app:
- "format_2:formatted_data.*" - returns None
- "format_2:formatted_data" - returns "192.168.0.1, 192.168.0.2" as one string
So, how to make 2 different requests here?
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
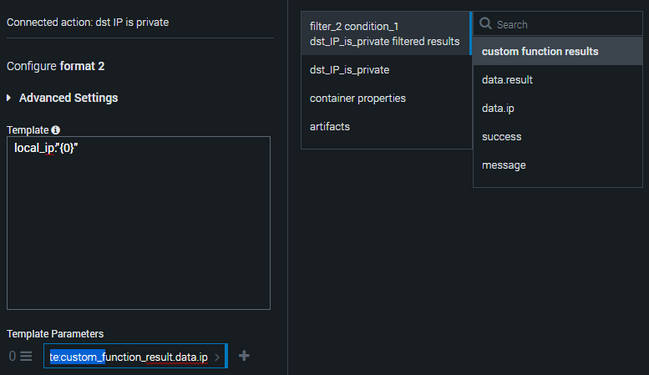
@Izzet if you use the format block's list interpretation (https://docs.splunk.com/Documentation/Phantom/4.9/PlaybookAPI/PlaybookAPI#format) then you can use the .* output.
In your format block you should put:
%%
local_ip:{0}
%%
Then when you use the .* output the action block knows it's getting a list and will create the relevant for loop to iterate though each one.
As a side note, did you know the filter/decisions are CIDR aware? So you can use them to determine if they are in a known CIDR range (internal/RFC1918) or not without a custom function 😄
For example you can put the IP (single or list) into the top field in a filter/decision condition, then use 'is in' then put the CIDR range in the final condition field, see below:
<IP_VALUE>
is in
192.168.0.0/16
If this helped please drop a like below!