- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Enterprise
- :
- help on eval command linked to a time input token
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
as you can see in my xml, I use an eval command in order to define an health status
this eval command is linked to a token time
now I would like to correlate the rule of my eval command with the time token
For example, if I choose the "last 7 days" in my time token, the hang has to be > 5 and the crash > 2
But if i choose the "last 30 days" in my time token, the hang has to be > 1 and the crash > 4
how to do this please?
<form theme="dark">
<search id="bib">
<query> index=toto ((sourcetype="hang") OR ( sourcetype="titi")
OR (sourcetype="tutu" web_app_duration_avg_ms > 7000))
</query>
<earliest>$date.earliest$</earliest>
<latest>$date.latest$</latest>
</search>
<input type="time" token="date" searchWhenChanged="true">
<label>Période</label>
<default>
<earliest>-7d@h</earliest>
<latest>now</latest>
</default>
</input>
</fieldset>
<row>
<panel>
<single>
<search base="bib">
<query>| stats count(hang_process_name) as hang, count(crash_process_name) as crash by site
| eval sante=if((hang>5) AND (crash>2), "Etat de santé dégradé","Etat de santé acceptable")
</query>
</search>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the title to investigate the value of the label
<label>$pickerlabel$</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
<change>
<condition label="Last 30 days">
<eval token="pickerlabel">label</eval>
<set token="hangmin">200</set>
<set token="crashmin">200</set>
</condition>
<condition label="Last 7 days">
<eval token="pickerlabel">label</eval>
<set token="hangmin">100</set>
<set token="crashmin">100</set>
</condition>
<condition>
<!-- Default values for these tokens -->
<eval token="pickerlabel">label</eval>
<set token="hangmin">1</set>
<set token="crashmin">1</set>
</condition>
</change>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add a change handler to the timepicker:
<change>
<condition label="Last 30 days">
<set token="hangmin">1</set>
<set token="crashmin">4</set>
</condition>
<condition label="Last 7 days">
<set token="hangmin">5</set>
<set token="crashmin">2</set>
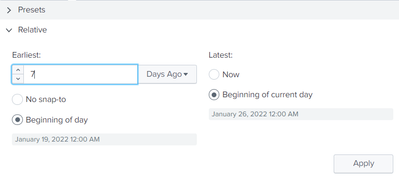
</condition>However, some of the labels don't equate to what you might expect. For example, "Last 7 days" from the presets ends up with a label of "Custom time" (at least in the version of Splunk I am using), but if you use relative 7 days ago to now snapped to start of day, you can get a label of "Last 7 days"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry I dont understand to apply
what I have to modif in my eval command?
<form>
<label>SANTE</label>
<fieldset submitButton="true" autoRun="true">
<input type="time" token="field1" searchWhenChanged="true">
<label>sss</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
</input>
</fieldset>
<row>
<panel>
<single>
<search>
<query>index=toto sourcetype=tutu
| stats count(hang_process_name) as hang, count(crash_process_name) as crash by site
| eval sante=if((hang>5) AND (crash>2), "Etat de santé dégradé","Etat de santé acceptable")
| eval severity=if(sante="Etat de santé dégradé",1,0)
| rangemap field=severity low=0-0 default=severe</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<option name="height">50</option>
</single>
</panel>
</row>
</form>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<form>
<label>SANTE</label>
<fieldset submitButton="true" autoRun="true">
<input type="time" token="field1" searchWhenChanged="true">
<label>sss</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
<change>
<condition label="Last 30 days">
<set token="hangmin">1</set>
<set token="crashmin">4</set>
</condition>
<condition label="Last 7 days">
<set token="hangmin">5</set>
<set token="crashmin">2</set>
</condition>
<condition><!-- Default values for these tokens -->
<set token="hangmin">1</set>
<set token="crashmin">1</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<single>
<search>
<query>index=toto sourcetype=tutu
| stats count(hang_process_name) as hang, count(crash_process_name) as crash by site
| eval sante=if((hang>$hangmin$) AND (crash>$crashmin$), "Etat de santé dégradé","Etat de santé acceptable")
| eval severity=if(sante="Etat de santé dégradé",1,0)
| rangemap field=severity low=0-0 default=severe</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<option name="height">50</option>
</single>
</panel>
</row>
</form>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
something is not working
for example, if I modify the condition for the last 7 days
<condition label="Last 7 days">
<set token="hangmin">50</set>
<set token="crashmin">4</set>a site is considered as "Etat de santé dégradé" instead of "Etat de santé acceptable" because his results are under the threshold of hangmin and crashmin....
I dont understand what is wrong...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How have you selected Last 7 days?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I said earlier, this doesn't work, you need to use relative, not the preset
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes I done it too
And no matter the hangmin and the crashmin I define the sante is always "Etat de santé dégradé" for this specific site...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
here is
<form>
<label>SANTE</label>
<fieldset submitButton="true" autoRun="true">
<input type="time" token="field1" searchWhenChanged="true">
<label>sss</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
<change>
<condition label="Last 30 days">
<set token="hangmin">200</set>
<set token="crashmin">200</set>
</condition>
<condition label="Last 7 days">
<set token="hangmin">100</set>
<set token="crashmin">100</set>
</condition>
<condition>
<!-- Default values for these tokens -->
<set token="hangmin">1</set>
<set token="crashmin">1</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<title>XXX</title>
<table>
<search>
<query>index=tutu sourcetype=toto
| stats count(hang_process_name) as hang, count(crash_process_name) as crash by site
| eval sante=if((hang>$hangmin$) AND (crash>$crashmin$), "Etat de santé dégradé","Etat de santé acceptable")
| eval severity=if(sante="Etat de santé dégradé",1,0)
| rangemap field=severity low=0-0 default=severe
| table site sante hang crash</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
<option name="drilldown">row</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>
</form>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share your current SimpleXML?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<form>
<label>SANTE</label>
<fieldset submitButton="true" autoRun="true">
<input type="time" token="field1" searchWhenChanged="true">
<label>sss</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
<change>
<condition label="Last 30 days">
<set token="hangmin">200</set>
<set token="crashmin">200</set>
</condition>
<condition label="Last 7 days">
<set token="hangmin">100</set>
<set token="crashmin">100</set>
</condition>
<condition>
<!-- Default values for these tokens -->
<set token="hangmin">1</set>
<set token="crashmin">1</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<title>XXX</title>
<table>
<search>
<query>index=toto
| fields hang_process_name crash_process_name site
| stats count(hang_process_name) as hang, count(crash_process_name) as crash by site
| eval sante=if((hang>$hangmin$) AND (crash>$crashmin$), "Etat de santé dégradé","Etat de santé acceptable")
| eval severity=if(sante="Etat de santé dégradé",1,0)
| rangemap field=severity low=0-0 default=severe
| table site sante hang crash</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
<option name="drilldown">row</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>
</form>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try changing the label of the timepicker to show what the values of the token are
<label>$hangmin$ $crashmin$</label>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know what the value are because I have added
| table site sante hang crashso I can see the input time token is not working correctly
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This doesn't tell you the value of the tokens being used in your if statement - you need to debug the timepicker change handler to determine which values are being set in the tokens - I think there is a token debugger app in splunkbase that you could try if simply displaying them in labels doesn't work for you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have found
Its due to the language...
If I replace "Last 7 days" by "Dernière 7 jours" it works
But it doesnt works for 30 j!
I dont understand
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the title to investigate the value of the label
<label>$pickerlabel$</label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
<change>
<condition label="Last 30 days">
<eval token="pickerlabel">label</eval>
<set token="hangmin">200</set>
<set token="crashmin">200</set>
</condition>
<condition label="Last 7 days">
<eval token="pickerlabel">label</eval>
<set token="hangmin">100</set>
<set token="crashmin">100</set>
</condition>
<condition>
<!-- Default values for these tokens -->
<eval token="pickerlabel">label</eval>
<set token="hangmin">1</set>
<set token="crashmin">1</set>
</condition>
</change>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is anybody can help please?