- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Enterprise
- :
- SC4S - PaloAlto logs not processed correctly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SC4S - PaloAlto logs not processed correctly
Hi,
I am trying to configure PaloAlto logs via the Splunk Connect for Syslog.
I followed the instructions here
https://splunk.github.io/splunk-connect-for-syslog/main/sources/PaloaltoNetworks/
I configured the syslog at PaloAlto according the instructions. I also c
I can see the syslog connections arriving to the host from the firewall using the command tcpdump port 514.
Add the following lines to splunk_metadata.csv
pan_config,index,test
pan_correlation,index,test
pan_globalprotect,index,test
pan_hipmatch,index,test
pan_log,index,test
pan_system,index,test
pan_threat,index,test
pan_traffic,index,test
pan_userid,index,test
And restart sc4s
systemctl restart sc4s
I checked the index test and it is empty. I enabled the debug by adding with the line in the env_file
SC4S_DEST_GLOBAL_ALTERNATES=d_hec_debug
and it seems like the index defined in the spplunk_metadata.csv is not taken, instead osnix is used.
curl -k -u "sc4s HEC debug:$SC4S_DEST_SPLUNK_HEC_DEFAULT_TOKEN" "https://splunk.XX.XXX.XXu:8088/services/collector/event" -d '{"time":"1643726324.000","sourcetype":"nix:syslog","source":"program:","index":"osnix","host":"atlas-fw-01.XXX.XX.XX","fields":{"sc4s_vendor_product":"nix_syslog","sc4s_syslog_severity":"info","sc4s_syslog_format":"rfc5424_strict","sc4s_syslog_facility":"user","sc4s_proto":"UDP","sc4s_loghost":"xxxxxxxxxx","sc4s_fromhostip":"192.168.10.100","sc4s_destport":"514","sc4s_container":"xxxxxxxx"},"event":"2022-02-01T14:38:44.000+00:00 atlas-fw-01.xxx.xxx.xxx - - - - 1,2022/02/01 15:38:43,011901021137,TRAFFIC,end,2561,2022/02/01 15:38:43,192.168.20.63,157.240.27.54,154.14.118.254,157.240.27.54,Normal traffic,xxx\\yyy,,quic,vsys1,Internal,External,ae1,ae2.6,Splunk,2022/02/01 15:38:43,113676,1,56081,443,49985,443,0x400019,udp,allow,7358,2250,5108,19,2022/02/01 15:36:43,0,any,,7030011678692056750,0x0,192.168.0.0-192.168.255.255,Germany,,7,12,aged-out,0,0,0,0,,atlas-fw-01,from-policy,,,0,,0,,N/A,0,0,0,0,c8250554-4ccd-46e3-8498-e74cfe9cdd10,0,0,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,2022-02-01T15:38:44.130+01:00,,,infrastructure,networking,browser-based,1,tunnel-other-application,,quic,no,no,0"}'
I already check and the HEC token is allowed to index test.
Could someone tell me what is happening?
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I reply myself here for future reference, it might help others.
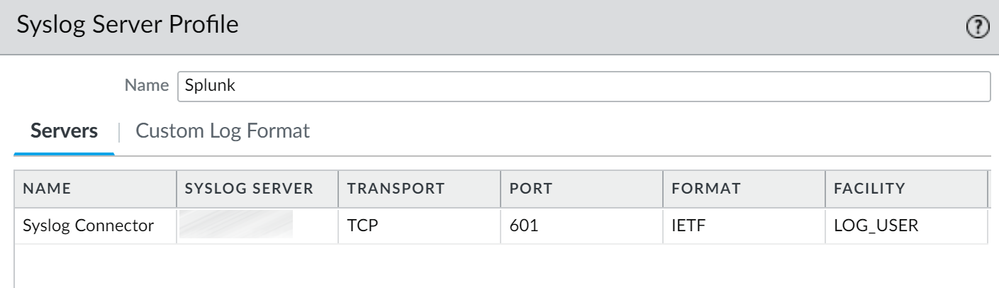
My issue was finally solved and it was due to the format PaloAlto produces the syslog events. to be compatible with SC4S, we need to configure PaloAlto to send the logs to port 601 in TCP and with the format EITF.
Then, in the SC4S host , you might need to open the flow in the local firewall , in my case it was firewalld.
firewall-cmd --permanent --add-port 601/tcp
firewall-cmd --runtime-to-permanent
firewall-cmd --reload
finally the lines in the splunk_metadata.csv, in my case to use a different index.
pan_traffic,index,pan_logs
pan_config,index,pan_logs
pan_correlation,index,pan_logs
pan_globalprotect,index,pan_logs
pan_hipmatch,index,pan_logs
pan_log,index,pan_logs
pan_system,index,pan_logs
pan_threat,index,pan_logs
pan_userid,index,pan_logs
and that is all. I hope it helps someone.