- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Enterprise
- :
- Re: On what basis does the Universal Forwarder det...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
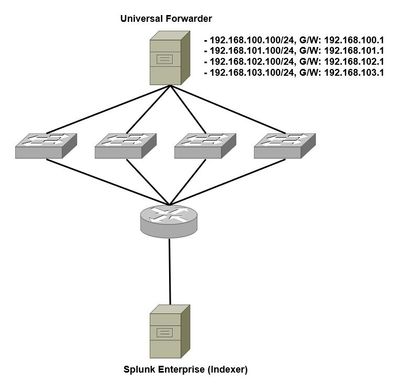
As shown in the picture below, one workstation has 4 IP addresses (4 NIC) and sends Windows Event log to Splunk Indexer.
When I search the log collected in the indexer, I could confirm that the source IP address of logs was decided randomly among 4 IP addresses.
I don't know the source IP address is decided by what criteria, so I ask this question.
My question:
1. Is the source IP address decided by what criteria?
2. Is there function to decide the source IP address in the Universal Forwarder?
For your information, my network is a standalone network without external connection such as Web.
Kind regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The host's routing table determines the default destination for non-local traffic.
Typically, a host with multiple interfaces would have a single default route associated with the highest priority interface. In this example, non-local traffic would traverse eth0 and have source address 192.168.100.100:
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 101 0 0 eth1
192.168.102.0 0.0.0.0 255.255.255.0 U 102 0 0 eth2
192.168.103.0 0.0.0.0 255.255.255.0 U 103 0 0 eth3If you have multiple addresses associated with one interface, you should still have one default route:
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.102.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.103.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0If, however, you have multiple default routes, they may be selected in a round-robin fashion, and your source address would vary between .100.100, .101.100, .102.100, and .103.100.
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.101.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.102.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.103.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.102.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.103.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0Routing table or policy management varies by operating environment.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's also worth noting that there is no such thing as "source ip of logs" in a general sense.
Yes, you can in some cases get the ip of the connection and push it into a field (especially if you have some intermediate processing layer) but in general sense IP of a connection over which the data is pushed is one thing and data in the event itself is another thing. Especially in case of windows event logs which often do not include any form of ip information.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The host's routing table determines the default destination for non-local traffic.
Typically, a host with multiple interfaces would have a single default route associated with the highest priority interface. In this example, non-local traffic would traverse eth0 and have source address 192.168.100.100:
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 101 0 0 eth1
192.168.102.0 0.0.0.0 255.255.255.0 U 102 0 0 eth2
192.168.103.0 0.0.0.0 255.255.255.0 U 103 0 0 eth3If you have multiple addresses associated with one interface, you should still have one default route:
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.102.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.103.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0If, however, you have multiple default routes, they may be selected in a round-robin fashion, and your source address would vary between .100.100, .101.100, .102.100, and .103.100.
$ route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.101.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.102.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.103.1 0.0.0.0 UG 100 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.102.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.103.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0Routing table or policy management varies by operating environment.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm grateful for your detailed explanation. Thanks to your help, I was able to understand it. Many thanks for your kind help.
Kind regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I understand it, the outbound NIC is selected by the operating system.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no other way. Splunk forwarder (and any other component) is typically run as a non-administrative user so has no way of performing low-level tasks like manipulating routing.
It just creates a socket and opens a connection to the destination server using OS library calls and the rest is up to the system.