- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Enterprise
- :
- How to filter incoming host facility messages in S...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to filter incoming host facility messages in Splunk?
Dear All,
I've got a question regarding syslog host facility information which can be send from a Huawei switch to Splunk. There is a facility command available on the Huawei switches which is meant for the possibility to categorize outgoing traffic to a remote syslogserver. I would like to know how to detect the facility information coming from the Huawei switch in Splunk and filter this type of information. Does anyone know how to filter the incoming traffic?
Related information:
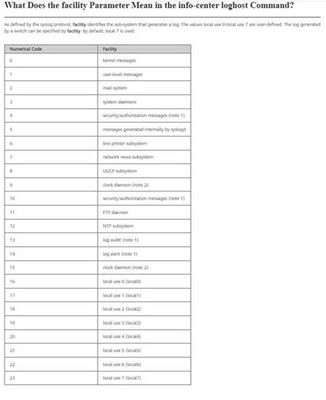
Facility > Specifies a syslog server facility that is used to identify the log information source. You can plan a local value for the log information of a specified device, so that the syslog server can handle received log information based on the parameter
In general there are channel groups and there are different log severity levels from 0 to 7 ( 0 = Emergencies 1= Alert , etc)
emergency alert critical error warning notice info debug
kernel 0 1 2 3 4 5 6 7
user 8 9 10 11 12 13 14 15
mail 16 17 18 19 20 21 22 23
system 24 25 26 27 28 29 30 31
security 32 33 34 35 36 37 38 39
syslog 40 41 42 43 44 45 46 47
lpd 48 49 50 51 52 53 54 55
nntp 56 57 58 59 60 61 62 63
uucp 64 65 66 67 68 69 70 71
time 72 73 74 75 76 77 78 79
security 80 81 82 83 84 85 86 87
ftpd 88 89 90 91 92 93 94 95
ntpd 96 97 98 99 100 101 102 103
logaudit 104 105 106 107 108 109 110 111
logalert 112 113 114 115 116 117 118 119
clock 120 121 122 123 124 125 126 127
local0 128 129 130 131 132 133 134 135
local1 136 137 138 139 140 141 142 143
local2 144 145 146 147 148 149 150 151
local3 152 153 154 155 156 157 158 159
local4 160 161 162 163 164 165 166 167
local5 168 169 170 171 172 173 174 175
local6 176 177 178 179 180 181 182 183
local7 184 185 186 187 188 189 190 191
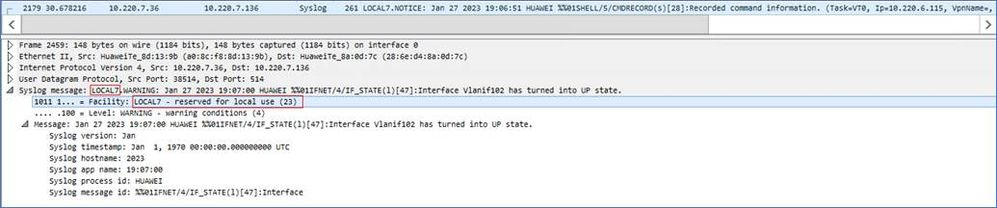
This facility field can used to easier identify some modules/processes from a device that generates log to your remote server. After the facility parameter is configured with the info-center loghost command, the switch will send the syslog packets containing the modified parameter, such as:
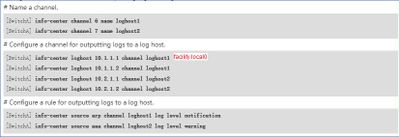
And for example if you mention specific source modules required to send logs to remote server, for that loghost you can modify the facility number contained in the packets, such as:
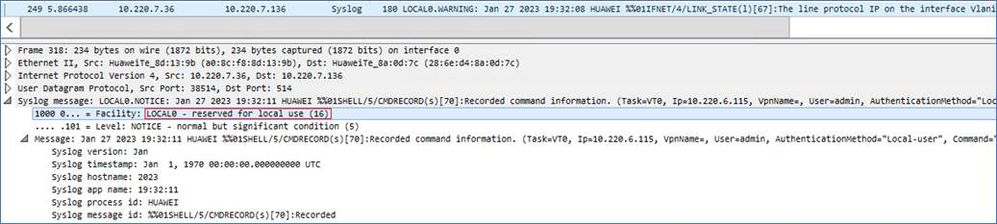
Here the ARP logs will be sent to loghost 1 using the user-defined local0 facility(number 16):
In the capture it will be changed like this:
So users can filter the logs with the facility field on the log server that supports the facility field. In the same time, if the remote server allows it, the facility can also be used to store the logs in different places based on this field. So specific logs with different facility fields can be categorized in specific paths for easier tracking. So combined with severity you can better find and track different sources that send syslog packets.
Help would be very appreciated.
Thanks in advance.
Best regards,
Danny