- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Enterprise
- :
- Re: How to extract the required keywords using REG...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to extract the required keywords using REGEX
Hello!
Log:
transactionId: NA, businesskey: GRNJob, environment: prod, flowName: app-report-grn-scheduler-flow, message: Computed Range for Aribus GRN Query - {"viewTemplateName":"mcdonalds_Receipt_updatedRange",
"filters": {
Based on the above log, I need to search in any logs for the message: "anything". Please help the regex to find out.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you are just looking for events with a match for "message:" followed by anything, not that you are trying to extract the "anything" into a field
| regex "message:\s[\w\s]+"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer as per our yesterday's discussion i got the exact results. So same like this in some of the events am not able to get like this the Message field is not taking up to extract while combining in Example 2.
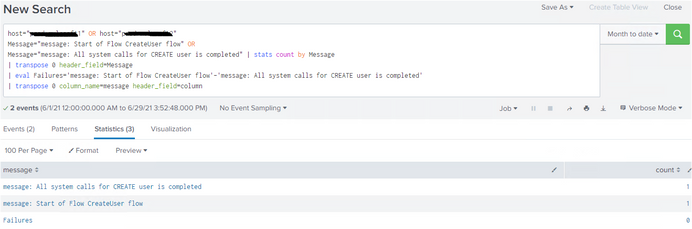
Example 1: Perfect output
host="mules1" OR host="mules2"
Message="message: Start of Flow CreateUser flow" OR
Message="message: All system calls for CREATE user is completed" | stats count by Message
| transpose 0 header_field=Message
| eval Failures='message: Start of Flow CreateUser flow'-'message: All system calls for CREATE user is completed'
| transpose 0 column_name=message header_field=column
Example 2: getting issue
but Individually showing events,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
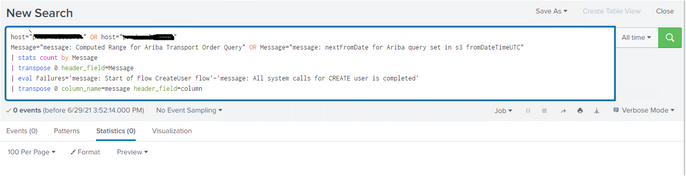
What events and what fields ar already extracted when you do this search?
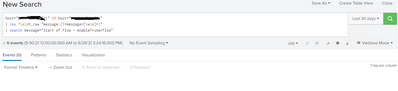
host="mules1" OR host="mules2" "nextFromDate for Ariba query set in s3 fromDateTimeUTC"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
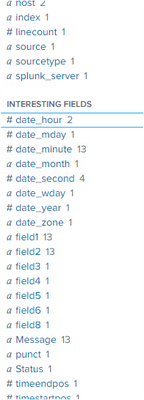
@ITWhisperer the events are related to "nextFromDate for Ariba query set in s3 fromDateTimeUTC" and the fields are below listed, in the files "Message" is extracted by me, based on that also some are not extracting under "Message" field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isn't that the issue - that that Message field extraction is not working for all your events?
Do you need to extract it in the search? Can you share your current extract configuration?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try replacing rex statement with
rex field=_raw "message:(?<message>[\w\s]+)" - Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on your sample can you try following it extracts message: <value>, value to a field called message, which you can further use to filter events.
Note: Regex only works for combination of numbers, Alphabets, space and _
From above sample value would be extracted as, message = Computed Range for Aribus GRN Query
index=<your_index> sourcetype=<your_sourcetype>
| rex "message:(?<message>[\w\s]+)"
| search message="<replace_it_with_string_you_want_to_search>"
---
An upvote would be appreciated and Accept Solution if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@venkatasri its not showing any results based on your query
I tried: No output
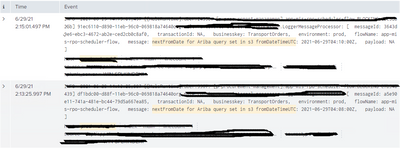
The output will be like this:
Search:
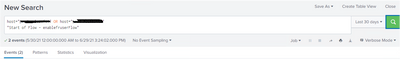
host="mules1" OR host="mules2" "nextFromDate for Ariba query set in s3 fromDateTimeUTC"
Output:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
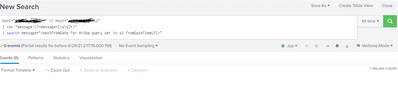
@phanichintha Originally there was no space in sample can you try this ,
Try | search =*nextFromDate for Ariba* something like this with wildcard there could be extra spaces being extracted.
index=<your_index> sourcetype=<your_sourcetype>
| rex "message:\s+(?<message>[\w\s]+)"
| search message="<replace_it_with_string_you_want_to_search>"