- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Where does the incident review saved filters get s...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to create a default search filter for ALL users that go into ES Incident Review. You can create a new filter but this I believe gets saved in your profile... I go into /splunk/etc/users and I would think the app that supports incident review would have it but nope. Ideas?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@cmeisch I haven't done extensive testing, but the only way using Saved Filters seems to be to copy the KVStore entry to each user's context (one entry for each user). For example, entries under nobody currently won't show up for any user.
You could alternatively add a link in your ES navigation that points to a default filter for Incident Review (or point users to a bookmarked URL for ES) that uses the correct URL parameters... for example:
/en-US/app/SplunkEnterpriseSecuritySuite/incident_review?earliest=-24h%40h&latest=now&status=0&status=1&status=2&status=3
See here for a little more details:
Hope that helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @cmeisch ,
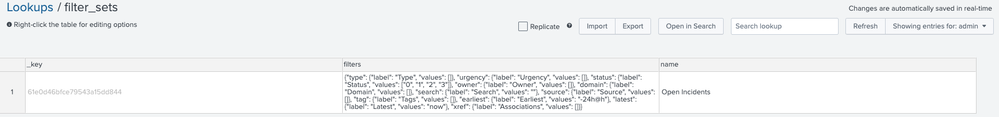
This is stored in a KV store collection named filter_sets in the SA-ThreatIntelligence application under the relevant user's context.
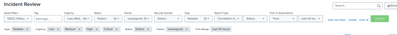
For example, if I have created a saved filter named Open incidents as the admin user as follows:
... Splunk will look at this REST endpoint:
/en-US/splunkd/__raw/servicesNS/admin/SA-ThreatIntelligence/storage/collections/data/filter_sets/61e0d46bfce79543a15dd844
Which contains:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to add to my previous post, beware of using the UI to update the filter_sets KV store, for example through the Splunk App for Lookup File Editing. Using that method is likely to save the JSON filter content as an escaped string, which will result in the Incident Review page not loading anymore (due to JS errors - which can be seen in the Browser JS Console).
Instead use the REST API endpoints directly (via curl or a script). Here an example that worked for me:
- Copy the JSON of a Saved Filter and adapt it if needed
- Insert the new Saved Filter into the filter_sets collection under the target user's context (named "test" in my example):
curl -k -u admin:changeme \
https://localhost:8089/servicesNS/test/SA-ThreatIntelligence/storage/collections/data/filter_sets \
-H 'Content-Type: application/json' \
-d '{"filters": {"type": {"label": "Type", "values": [] }, "urgency": {"label": "Urgency", "values": [] }, "status": {"label": "Status", "values": ["0", "1", "2", "3"] }, "owner": {"label": "Owner", "values": [] }, "domain": {"label": "Domain", "values": [] }, "search": {"label": "Search", "values": ""}, "source": {"label": "Source", "values": [] }, "tag": {"label": "Tags", "values": [] }, "earliest": {"label": "Earliest", "values": "-24h@h"}, "latest": {"label": "Latest", "values": "now"}, "xref": {"label": "Associations", "values": [] } }, "name": "Open Incidents", "_user": "admin"}'
- Re-read the newly added KV Store entry:
curl -k -u admin:changeme \
https://localhost:8089/servicesNS/test/SA-ThreatIntelligence/storage/collections/data/filter_sets
- Make sure the data returned is properly formatted JSON (as opposed to a escaped string) and note the _key value that was assigned.
- (Optionally) If you would like to make the new Saved Filter the default for the target user, add a defaultFilterSet entry with the _key value taken above to the user's user-prefs.conf file (under $SPLUNK_HOME/etc/users/test/user-prefs/local/user-prefs.conf). For example:
[general]
tz = America/New_York
search_use_advanced_editor = true
search_line_numbers = false
search_auto_format = false
defaultFilterSet = 64497a238e2e60128c6be2e3
Have the target log out and log back in again, and you should be all set.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the response and info @ccl0utier !!! My goal is to set a default filter for all who log into this ES. Is this possible?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@cmeisch I haven't done extensive testing, but the only way using Saved Filters seems to be to copy the KVStore entry to each user's context (one entry for each user). For example, entries under nobody currently won't show up for any user.
You could alternatively add a link in your ES navigation that points to a default filter for Incident Review (or point users to a bookmarked URL for ES) that uses the correct URL parameters... for example:
/en-US/app/SplunkEnterpriseSecuritySuite/incident_review?earliest=-24h%40h&latest=now&status=0&status=1&status=2&status=3
See here for a little more details:
Hope that helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SO Rock On! from the GUI one is able to create a default view and pass that to all the users. Bummer in that it looks like those settings are in a KV Store somewhere and not in a CONF?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you sir!!!