- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Visualisation : Single Value with Trendline
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Im trying to create a single value with trendline visualisation, where I want to compare the difference between todays result with yesterday results. The trendline should be the results difference of yesterday and today.
I have applied several solutions, but the total number does not tally with the today's result.
My base query is:
| stats count
which result shown as (today result) :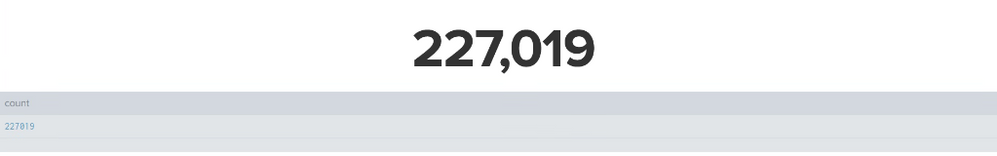
Here are several solutions that I have tried:-
Solution 1
Im using the trendline wma2
| timechart span=1d count as Total
| trendline wma2("x") as Trend
| sort - _time
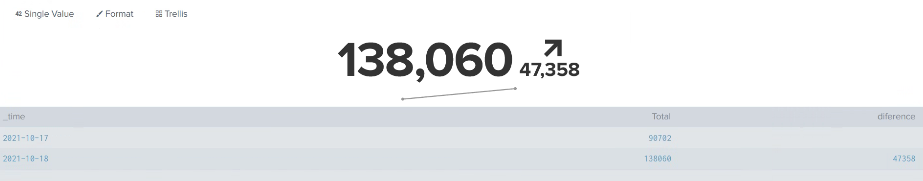
the result shown as below:
- the result shows the trendline, but the total number (90,702) did not tally with today's result (227,019).
Solution 2
Im using the delta command :-
| timechart span=1d count as Total
| delta Total p=1 as diference
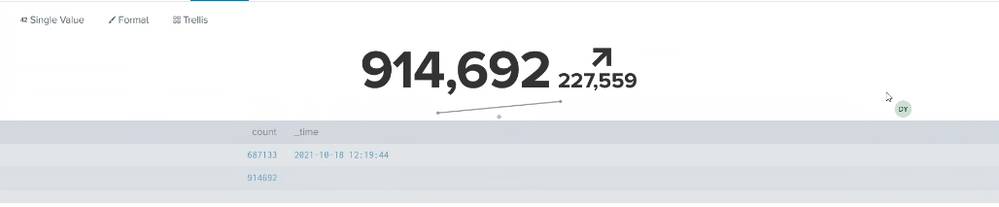
the result shown as below:
- the total number is different (including the trendline number)
Solution 3
I tried to use the |tstats command (from Enterprise Security)
| append
[| tstats summariesonly=true allow_old_summaries=true count from datamodel=Email where (All_Email.action=* AND All_Email.orig_dest!="" OR All_Email.orig_src!="") earliest=-24h latest=now]
| appendcols
[| makeresults
| eval time=now()
]
| rename time AS _time
- which also did not work
Can anyone help? Did i missed anything? Please.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi syazwani,
What timeframes are you specifying for your searches? I suspect that's the reason why you're getting inconsistencies in your search.
In your enterprise security search you're specifying a 24 hour time period:
earliest=-48h latest=-24hWhich will give you different results depending on the time you run it.
Try the following:
Todays current total:
index=emailgateway action=* from!="" to!="" earliest=@d
| stats count
Compare yesterday and today:
index=emailgateway action=* from!="" to!="" earliest=-1d@d
| timechart span=1d count as total
Simpler tstats command:
| tstats summariesonly=true allow_old_summaries=true count from datamodel=Email where All_Email.action=* All_Email.orig_dest!="" All_Email.orig_src!="" earliest=-1d@d latest=now by _time span=1d
Using earliest=-1d@d will take the search back to the beginning of yesterday (12:00am). Whereas using earliest=@d will take you to the beginning of the current day.
Hope this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi syazwani,
What timeframes are you specifying for your searches? I suspect that's the reason why you're getting inconsistencies in your search.
In your enterprise security search you're specifying a 24 hour time period:
earliest=-48h latest=-24hWhich will give you different results depending on the time you run it.
Try the following:
Todays current total:
index=emailgateway action=* from!="" to!="" earliest=@d
| stats count
Compare yesterday and today:
index=emailgateway action=* from!="" to!="" earliest=-1d@d
| timechart span=1d count as total
Simpler tstats command:
| tstats summariesonly=true allow_old_summaries=true count from datamodel=Email where All_Email.action=* All_Email.orig_dest!="" All_Email.orig_src!="" earliest=-1d@d latest=now by _time span=1d
Using earliest=-1d@d will take the search back to the beginning of yesterday (12:00am). Whereas using earliest=@d will take you to the beginning of the current day.
Hope this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi chef,
Yeah I messed up with the timeframes 🙂 Im using the comparison query and its working fine. Thankyou. This really helps me a lot. Thankyou again sir.