Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Enterprise Security
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Threat Artifacts setting
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
WildHuckleberry
Path Finder
01-27-2022
12:04 AM
Hello Splunkers,
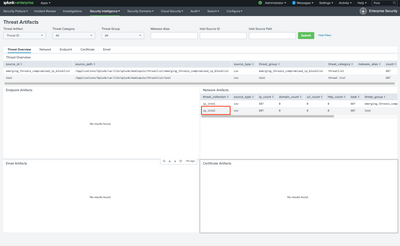
is there any way to change that red box name as a test??
Thank you in advance 🙂
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
isoutamo

SplunkTrust
01-27-2022
12:22 AM
Hi
just add in this panel's SPL next part
....
| eval threat_collection = if(threat_collection == "ip_intel", "Foo Bar", threat_collection)
| ....r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
isoutamo

SplunkTrust
01-27-2022
12:22 AM
Hi
just add in this panel's SPL next part
....
| eval threat_collection = if(threat_collection == "ip_intel", "Foo Bar", threat_collection)
| ....r. Ismo
Get Updates on the Splunk Community!
Extending Observability Content to Splunk Cloud
Watch Now!
In this Extending Observability Content to Splunk Cloud Tech Talk, you'll see how to leverage ...
More Control Over Your Monitoring Costs with Archived Metrics!
What if there was a way you could keep all the metrics data you need while saving on storage costs?This is now ...
New in Observability Cloud - Explicit Bucket Histograms
Splunk introduces native support for histograms as a metric data type within Observability Cloud with Explicit ...