- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- In Splunk Enterprise Security, how do you use a su...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Splunk Enterprise Security, how do you use a subsearch to correlate information?
Hello,
I'm trying to correlate events from 2 different source types, and 2 searches for example:
- sourcetypeA has fields IP_Address, MAC_Address, User
- sourcetypeB has the following fields: Time, IPAdd, hostname, DomainController. The IP Address field name is different from sourcetype A, ie: IPAdd, there are multiple events with the same pair, and I'm only searching events on a particular DomainController.
I would like to display a table with the following result with one line for each IP Address:
IP_Address, MAC_Address, User, hostname, DomainController
I tried to use a subsearch like this:
sourcetype=sourcetypeA
[search sourcetype=sourcetypeB DomainController="DC1"
| rename IPAdd as IP_Address | table IP_Address ]
| table Time, IP_Address, MAC_Address, User, hostname, DomainController
but it doesn't work. It only displays the values from the main search (SourcetypeA) (the fields from sourcetypeB are empty).
I'm not sure if a subsearch is the best way to do this? Any clue?
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are so close; try this:
index=YouShouldAlwaysSpecifyIndex_A AND sourcetype=AndSourcetypeToo_A AND
[ search index=YouShouldAlwaysSpecifyIndex_B AND sourcetype=AndSourcetypeToo_B AND DomainController="DC1"
| rename IPAdd AS IP_Address
| mvexpand IP_Address
| dedup IP_Address
| table IP_Address ]
| table _time, Time, IP_Address, MAC_Address, User, hostname, DomainController
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@lth186,
Give this a try and see if it works,
( sourcetype=sourcetypeA) OR (sourcetype=sourcetypeB DomainController="DC1")
|eval IP=coalesce(IP_Address,IPAdd )|fields Time, IP, MAC_Address, User, hostname, DomainController
|stats values(*) as * by IP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okie, tried to simulate your data and I got the results.
Please have a look and let me know the difference in your data/results
sourcetypeA has the following records:
IP_Address="1.1.1.1" , MAC_Address="AB:CD:ED:DF:SS",User="user1"
IP_Address="1.1.1.2" , MAC_Address="AB:CD:ED:DF:2S",User="user2"
IP_Address="1.1.1.3" , MAC_Address="AB:CD:ED:RF:SS",User="user3"
sourcetypeB has the following records:
Time="2019-02-09 01:00:00",IPAdd="1.1.1.1",hostname="PC1",DomainController="DC1"
Time="2019-02-09 01:01:00",IPAdd="1.1.1.1",hostname="PC2",DomainController="DC2" -->1.1.1.1 has both DC1 & DC2
Time="2019-02-09 01:02:00",IPAdd="1.1.1.2",hostname="PC3",DomainController="DC1"
Time="2019-02-09 01:03:00",IPAdd="1.1.1.3",hostname="PC4",DomainController="DC2" -->1.1.1.3 has only DC2
Search"
index=test ( sourcetype=sourcetypeA) OR (sourcetype=sourcetypeB DomainController="DC1")
|eval IP=coalesce(IP_Address,IPAdd )|fields Time, IP, MAC_Address, User, hostname, DomainController
|stats values(*) as * by IP
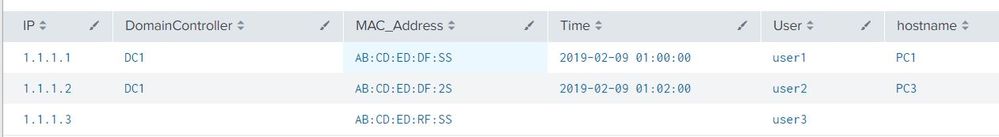
Result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@renjith.nair ,
Unfortunately it doesn't seems to work, the criteria in the second search (DomainController="DC1") doesn't seem to be taken into account, and only the fields from one sourcetype display correctly.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you search sourcetype=sourcetypeB DomainController="DC1" separately , do you have results?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes I have
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK,are they multivalue fields - a single row has more than one value?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are multiple rows, but one IP_Address has only one single hostname, for example
IP_Address1, PC1, DC1
IP_Address1, PC1, DC2
IP_Address2, PC2, DC2
IP_Address2, PC2, DC2
IP_Address3, PC3, DC1