- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Re: CIM malware actions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Greetings...
We are currently using ES and ingesting data from our IDS and AV to populate the Malware DataModel.
According to the documentation:
https://docs.splunk.com/Documentation/CIM/4.13.0/User/Malware
Dataset name: Malware_Attacks Field
name: action
Data type: string
Description: The action taken by the reporting device.
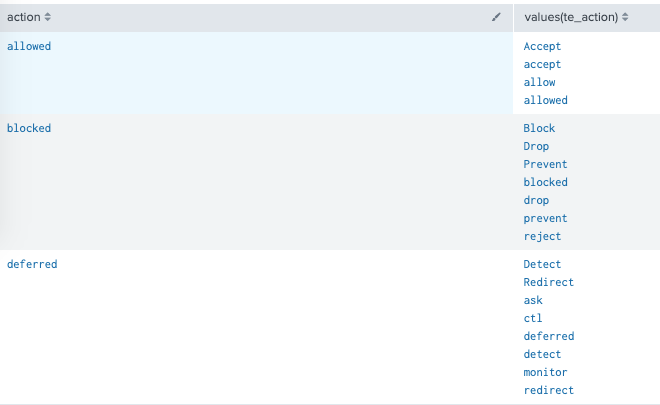
Abbreviated list of example values:
ES expects: allowed
Other: blocked, deferred
In our DataModel, we have an Eval Expression that uses a CSV inputlookup:
| inputlookup actions_te.csv
Which is not always helpful as there are a LOT of events being picked up by "deferred"
Would it still be CIM compliant if we evaled Redirect and Detect events as their own actions?
Would this break anything in ES?
Thanks in advance.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My suggestion is that you map your field values to one of - allowed/blocked/deferred for CIM complaince. this way the Security Domain -> Malware Center/Search/Operations dashboard will all be fine.
Any searches using datamodel/tstats should also be fine.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My suggestion is that you map your field values to one of - allowed/blocked/deferred for CIM complaince. this way the Security Domain -> Malware Center/Search/Operations dashboard will all be fine.
Any searches using datamodel/tstats should also be fine.