- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Cloud Platform
- :
- Is there an alternate command for collect?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there an alternate command for collect?
Hi ,
Do we have any command in splunk which does similar functionality like "Collect " command.
Can someone suggest on this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We cannot use "collect" command
Please see my example search:
index="main"
|table host index tag
|collect index="custom_index"
It didn't work. No results were collected in "custom_index"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have permissions to read the index? Do you have permissions to run the collect command? What search are you using to check whether events have been written?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have a new index named "threathunting" and having permission to collect the results. We use splunk admin account.
How do we check that we have permission to run collect command?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What search are you using to get the results from the summary index?
What does the job inspector say about the search you use to collect the events? (It should say something about successfully writing the results to stash.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the original command without |collect is working fine and gets results.
index="main"
|table host index tag
|head 10
Till this command, it shows the results with table. When I put the collect command, the search run has no error, still showing the head 10 results.
|collect index="threathunting"
But, the results are not collected in the "threathunting" index.
I already created a empty "threathunting" index, get permission and accessible index.
So, the head 10 results should be collected in "threathunting" index. Yet, it can't.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After you run the search with the collect command, even if there is no error, there should still be a message in the job. What messages do you get when you click on the job button
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Successfully wrote file to '/opt/splunk/var/spool/splunk/b90a7184a4568807_events.stash_new'.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you go to settings -> indexes, what does it say about your index?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Setting>Indexes>threathunting
It's enabled, deployed in the Global sharing permissions app. It also has home path for db.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like no events in the index - do you have any errors in the splunkd.log?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, "threathunting" index is empty and created to collect search results.
No error in splunkd.log
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does your original search return any results at all? (Without the collect part)
It doesn't seem right or at least doesn't seem like good practice to have events in the main index.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the original command without |collect is working fine and gets results.
index="main"
|table host index tag
Till this command, it shows results as table.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this a clustered environment? Do you have access to the file system and is the stash file still there?
Check the _internal index for any evidence of that stash file
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
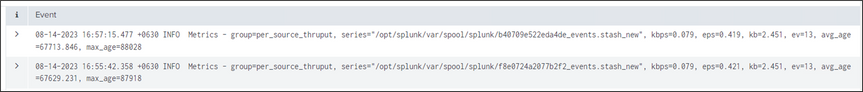
Yes, it was found in _internal index.
Also, this is a cluster environment. We have access to file system but there is no *_events.stash_new file under the /opt/splunk/var/spool/splunk/ directory.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this is clustered and your 'index' is showing no events, then I suspect there may be something going on with one index being on the search head and one on the indexer and you have an issue with data being ingested to one index rather than the other.
That sounds like an admin issue and I am not sure how to verify that.
Did you create the threathunting index through the UI on the search head - if so, that means the index is on the SH, not the indexers. Creating indexes on the indexers is not done through the UI, it needs to be set up in the conf files for the indexers.
If this is the case, I suspect the data is being "ingested" to a threathunting index that does not exist on the indexer, as you created it on the search head.