- Splunk Answers
- :
- Using Splunk
- :
- Other Usage
- :
- Re: search with multiple CSV
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to search with multiple CSV
Hello,
I'm currently using two csv to make an report as
- index A : file A CSV
-index B : file B CSV
I m trying to add an value from raw csv file A into raw csv file B.
With my first search form CSV file B I get this values
| Owner | IP |
| Owner A | 10.10.10.2 |
| Owner B | 10.10.10.3 |
I would like to add the Owner value from my first search into my second search...
| Owner -> I would get from file A | IP -> same value as ip into file A | CVE | Risk |
| Owner A | 10.10.10.2 | ||
| Owner B | 10.10.10.3 |
How can get value of Owner from csv file B and add them on my search ?
Regards,
Miguel
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are many ways to achieve this, some are more efficient than others. To receive more accurate suggestions, please share your current search (mask anything sensitive). A general way would be this
search indexA OR search index=B
| fields Owner IP CVE Risk
| stats values(*) as * by IP- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Thank you for your answer, I will you explain my case better.
I have two CSV file with csv file A where the content is some CVE vulnerability by ip server and the second CSV file B where the content is the list of our server where is mentionned the server owner etc.
I want to show on the dashboard the Owner, name server, CVE, IP ect.
In the csv file A the Owner is not associed with the IP server so I did an variable "ip" to merge the data from both CSV and get the owner associed with the IP with "transaction"
(index="A" AND (Risk=$Risk$))OR(index="B" AND ("Deployment State"=Production))| eval ip_extracted=if(cidrmatch("Network",extracted_Host), "ipok", "noip") | eval ip_servers=if(cidrmatch("Network",NIC__1__IPAddress__1), "ipok", "noip") | eval ip=if(match(ip_servers, "ipok"),NIC__1__IPAddress__1, extracted_Host) | transaction ip | table Owner ip Risk Name Description Solution "CVSS v2_0 Base Score" "CVSS v3_0 Base Score" OperatingSystem | where Risk!="NULL" |search Owner=$Owner$ ip=$ip$
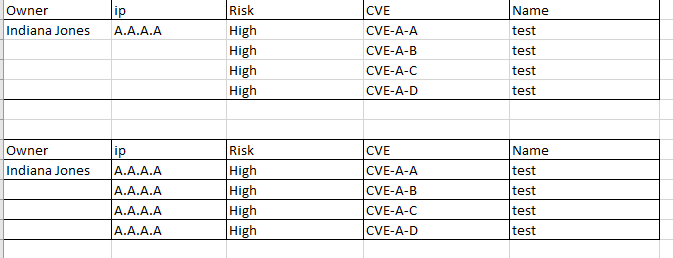
Now my problem is that each events sorted by ip are merged in my dashboard, I want that each event is shown independently by ip like as shown below because I want to add an check case where the owner can check if the event has been done or not and actualy it's not possible because each events are merged
My English is not good so I don't know if you have understand what I mean ?
Regards,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
(index="A" AND (Risk=$Risk$))OR(index="B" AND ("Deployment State"=Production))
| eval ip_extracted=if(cidrmatch("Network",extracted_Host), "ipok", "noip")
| eval ip_servers=if(cidrmatch("Network",NIC__1__IPAddress__1), "ipok", "noip")
| eval ip=if(match(ip_servers, "ipok"),NIC__1__IPAddress__1, extracted_Host) | fields Owner ip Risk Name Description Solution "CVSS v2_0 Base Score" "CVSS v3_0 Base Score" OperatingSystem
| stats values(*) as * by ip | where Risk!="NULL" |search Owner=$Owner$ ip=$ip$- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
thx for your reply but the result it's same, all events are merged