- Splunk Answers
- :
- Using Splunk
- :
- Reporting
- :
- Re: Date formatted fine in dashboard but incorrect...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
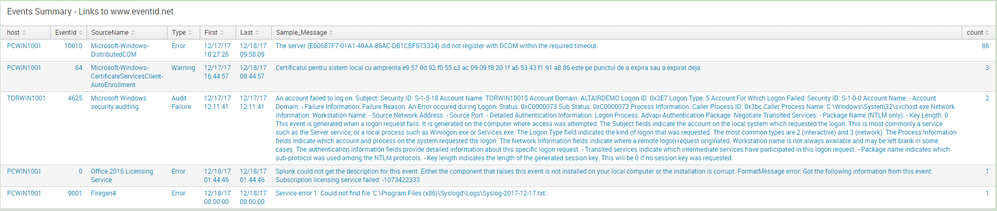
I have a report created from one of the Windows Event Logs Analysis App dashboards. The dashboards displays the first and last time for the Windows events in scope of the search and the timestamps are displayed as expected:
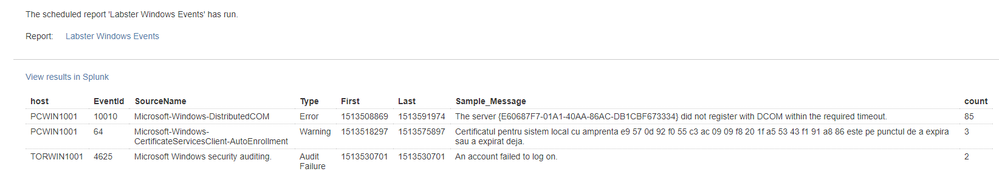
However, a report created from the same search displays the date in Unix format when sent by email. For example, 1513508869 instead of 12/17/17 10:27:26:
The search command is:
`event_sources`
| fillnull
| eval Type=if(Keywords=="Audit Success",Keywords, Type)
| eval Type=if(Keywords=="Audit Failure",Keywords, Type)
| search ((Type="Error" OR Type="Warning") OR (Type="Denial" OR Type="Audit Failure"))
| stats earliest(_time) as First latest(_time) as Last max(Message) as Sample_Message count by host, EventCode, SourceName, Type
| sort -count host, EventCode, SourceName, Type
| rename EventCode as "EventId"
| fieldformat First=strftime(First,"%x %X")
| fieldformat Last=strftime(Last,"%x %X")
event_sources is a macro that specifies where the Windows event logs are indexed.
Is this a bug or a limitation of the emailed reports?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect that fieldformat is not respected in exporting to reports, much as it's not supported for exporting to CSVs or lookups.
The fieldformat command does not apply to commands that export data, such as the outputcsv and output lookup commands. The export retains the original data format and not the rendered format. If you want the format to apply to exported data, use the eval command instead of the fieldformat command.
https://docs.splunk.com/Documentation/Splunk/7.0.1/SearchReference/Fieldformat
As suggested in the docs above, you may need to use eval instead to get the result you're looking for.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect that fieldformat is not respected in exporting to reports, much as it's not supported for exporting to CSVs or lookups.
The fieldformat command does not apply to commands that export data, such as the outputcsv and output lookup commands. The export retains the original data format and not the rendered format. If you want the format to apply to exported data, use the eval command instead of the fieldformat command.
https://docs.splunk.com/Documentation/Splunk/7.0.1/SearchReference/Fieldformat
As suggested in the docs above, you may need to use eval instead to get the result you're looking for.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer, it did the trick. I've adjusted the search as:
`event_sources`
| fillnull
| eval Type=if(Keywords=="Audit Success",Keywords, Type)
| eval Type=if(Keywords=="Audit Failure",Keywords, Type)
| search ((Type="Error" OR Type="Warning") OR (Type="Denial" OR Type="Audit Failure"))
| stats earliest(_time) as First latest(_time) as Last max(Message) as Sample_Message count by host, EventCode, SourceName, Type
| eval First=strftime(First,"%x %X")
| eval Last=strftime(Last,"%x %X")
| sort -count host, EventCode, SourceName, Type
| rename EventCode as "EventId"
| table host,EventCode,SourceName,Type,First,Last,Sample_Message,count
and the date is shown in the report as expected.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! Glad to help.