- Splunk Answers
- :
- Splunk Administration
- :
- Monitoring Splunk
- :
- Re: Exceptions that never happened before
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys,
I will try to describe my problem as good as i can. I want to get some raport/alert when a new exception appears but that never happened before.
let say that i have 15 exceptions that happened before like: java.lang.NullPointer, java.lang.IllegalStateException.. etc.
i want to get an alert when a “new” exception appear that never appeared before.
Is that possible?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can. You will need to keep a record of exceptions that you have seen before in a lookup file, so that when you run a search you can then lookup against that file.
Here is some very pseudo SPL that can be used, but you will need to tailor it to your data and use case.
index=my_index *Exception*
``` Work out what is your exception here using some eval statemsnt or field extractions ```
| eval ExceptionName=...
| lookup my_previous_exceptions.csv ExceptionName OUTPUT ExceptionName as FoundExceptionName
| where isnull(FoundExceptionName)
``` Now you have events that contain new exceptions, ```
``` you can finally merge the new and existing exceptions that new Exception to your lookup ```
| fields ExceptionName _time
| outputlookup append=t my_previous_exceptions.csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can. You will need to keep a record of exceptions that you have seen before in a lookup file, so that when you run a search you can then lookup against that file.
Here is some very pseudo SPL that can be used, but you will need to tailor it to your data and use case.
index=my_index *Exception*
``` Work out what is your exception here using some eval statemsnt or field extractions ```
| eval ExceptionName=...
| lookup my_previous_exceptions.csv ExceptionName OUTPUT ExceptionName as FoundExceptionName
| where isnull(FoundExceptionName)
``` Now you have events that contain new exceptions, ```
``` you can finally merge the new and existing exceptions that new Exception to your lookup ```
| fields ExceptionName _time
| outputlookup append=t my_previous_exceptions.csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, depending on your data, you will have an event containing some information containing the text of the Exception, whether it's a full stack trace or just the exception name, but let's assume that your Splunk event contains
bla bla bla java.lang.NullPointerException bla bla bla
then unless you have a field in the data that has the name of the exception you need to create a field, either through an eval statement or a rex field extraction
If you don't have a field in the data, then you would use a rex statement, e.g. one of these would extract either the simple name or the full class name
| rex "(\w+\.)+(?<ExceptionName1>.*Exception) "
| rex "(?<ExceptionName2>(\w+\.)+\w+Exception) "an eval statement could be used to manipulate an existing field.
All of this will depend on what your data looks like though.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@bowesmana
Thank you a lot for your time, could tou show me how the las version of the search should look like with the “rex”
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will have to show what you are currently doing, where your data exists and the results you are getting to get further help. I can't provide direct searches without knowing your environment.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have message you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you explain me how do i do the backup file?
Like an example..
im pretty new.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't know what you mean by a backup file in Splunk context
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have write you in private.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please post the examples here, so any solutions can help others. I do not give answers through private messages.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you help me?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What exactly are you stuck with?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, even if i make the search wiht the data that i have is showing me all the exception, is not excluding the exception from the .csv.
How exactly should i make the search to get only the exception that are not in the file?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please post your current search and an example of the contents of the csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Currently im trying to search against this file :
index="doc" Exception error NOT [ | inputlookup KnownException.csv]
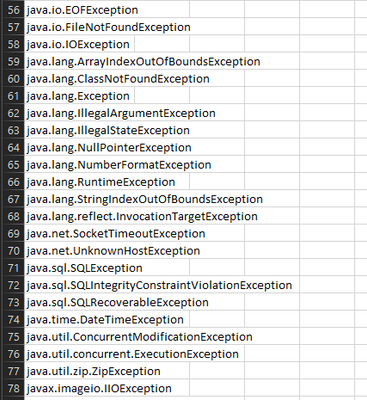
My csv file looks like this(140 exceptions):
My env looks like this:
When i run this query i want to extract only the exceptions that are not in the file. Somehow this is not happening and is showing me even the exceptions that are present in the file.
I want to full exclude all the exceptions from the file.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the column name of the field in your exception CSV?
Your subsearch will translate to
( ( Field = A) OR (Field = B) OR (Field = C) )where Field is the name of the column in your CSV and therefore MUST also be a field in your data. If it is not a field in your data, then you will be looking for event that do NOT contain those Fields, which will be everything.
You can also add this to your subsearch
| return 200 $FieldWhere 'Field' is the name of your column in the CSV and it will return just the text of the exception in the csv.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, the column is called "exception" and i don't have that column extracted as a field?
What you recommend?
And also how should look the final search ?
Thank you so much for the time and help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried my second suggestion?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content