- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How do I correct my configurations for proper Splu...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have a problem with the Splunk timestamp.
I know that when you have a problem with timestamp, you can modify this 2 ways:
1. Add data and modify the timestamp during the steps of adding manually data on Splunk.
2. Modify the props.conf
The problem :
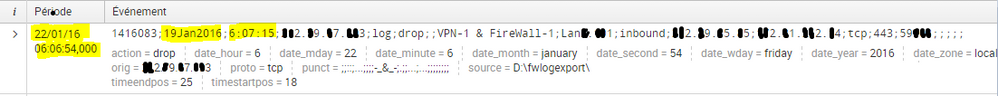
As we can see, on my log, the real timestamp is not the same compared to the timestamp recognized by Splunk.
For the First Way:
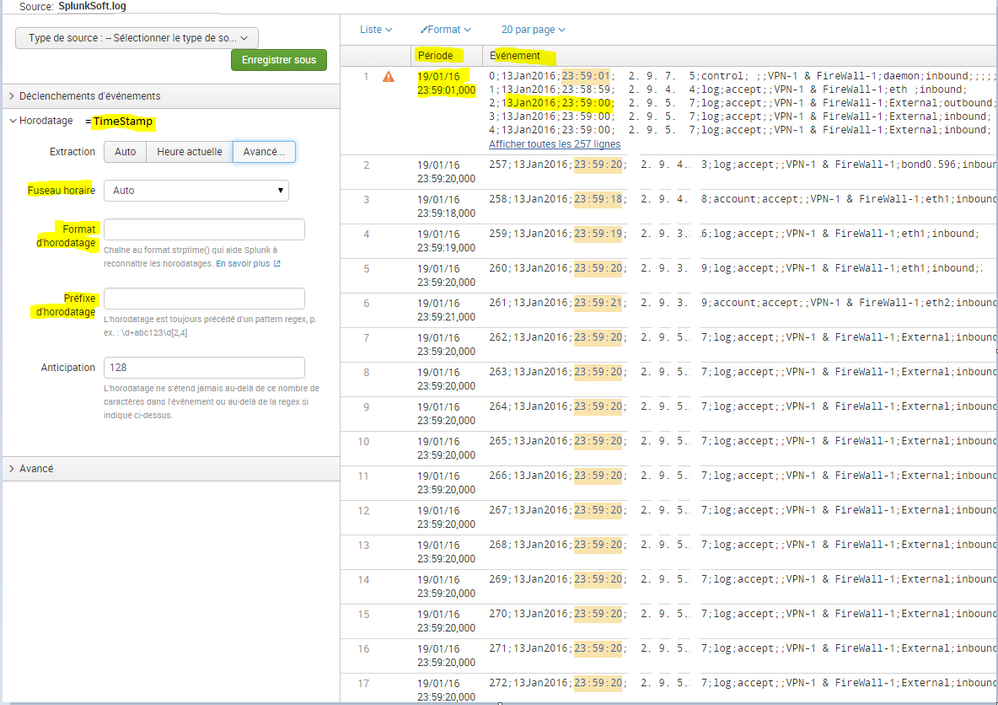
- 1.1 Adding Data manually and modify the timestamp steps by steps :
As we can see, Splunk recognizes the time, but not the date correctly, so I will modify the timestamp with the parameter on the left ( prefix and format)
- 1.2 So I will add the correct parameter:
--> I add the format and prefix, Splunk seem to recognize this correctly
(but the prefix is strange because it works also when I write d{2}; or d{1}; or d*; ... )
- At the final step, when I apply this ... nothing works after when I want to search something or when i just want to look the logs event. Nothing happens and I see the message that Splunk is waiting for queued job to start.
For the Second Way
edit props.conf
- There is so many props.conf, so to be sure, which one do I have to modify? I guess this one: Splunk/etc/apps/search/local ?
- And what do I have to add exactly?
I guess it is
TIME_PREFIX =... andTIME_FORMAT=...
Then after adding these parameters with the values, is there something else to modify to complete the configuration? Because even with this way, nothing happens and that doesn't work for me.
I missed something maybe, but I don't know what...
Kind Regards
Steve
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Add data wizard, add following parameters. Same things can be added to props.conf directly as well.
SHOULD_LINEMERGE = false
LINE_BREAKER = ([\r\n]+)\d+;\S+
TIME_FORMAT = %d%a%Y %H:%M:%S
TIME_PREFIX = ^\d+;
Remember to restart Indexer/Heavy forwarder where you keep this props.conf
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Add data wizard, add following parameters. Same things can be added to props.conf directly as well.
SHOULD_LINEMERGE = false
LINE_BREAKER = ([\r\n]+)\d+;\S+
TIME_FORMAT = %d%a%Y %H:%M:%S
TIME_PREFIX = ^\d+;
Remember to restart Indexer/Heavy forwarder where you keep this props.conf
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great thanks for your help guys 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The props.conf file to modify is the one for the app that will process the events. If it's the Search & Reporting app then SPLUNK_HOME/etc/apps/search/local/props.conf is the correct file. You should not need TIME_PREFIX. It should be enough to set TIME_FORMAT=%d%a%Y %H:%M:%S. Note that you must restart Splunk for the change to take effect and the change only applies to new data (nothing can be done about events that are already in Splunk).
If this reply helps you, Karma would be appreciated.