- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Help with inputs.conf Stanza for the Azure AD MFA ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all
Getting this message :
ERROR ExecProcessor [3700 ExecProcessor] - message from ""C:\Program Files\SplunkUniversalForwarder\bin\splunk-winevtlog.exe"" splunk-winevtlog - WinEventMon::configure: Failed to find Event Log with channel name='Microsoft-AzureMfa-AuthZ/AuthZAdminCh'
I've tried numerous combinations in the stanza such as :
WinEventLog://Microsoft-AzureMfa-AuthZ/AuthZAdminCh
WinEventLog://Microsoft-AzureMfa-AuthZ-AuthZAdminCh
WinEventLog://Microsoft/AzureMfa/AuthZ/AuthZAdminCh
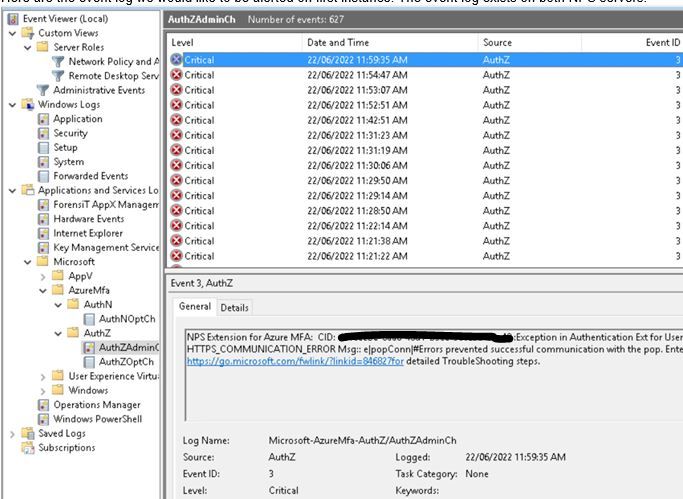
The Windows Event Log chain for the AuthZAdminCh source is in the attachment. Just not quite sure where I'm going wrong.
Appreciate some advice.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Powershell (get-winevent -listlog *).logname revealed that the channel is simply called "AuthZAdminCh"
( despite hierarchical ordering under Microsoft-AzureMfa-AuthZ as presented in Event viewer )
The proven stanza is as simple as : [WinEventLog://AuthZAdminCh]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Powershell (get-winevent -listlog *).logname revealed that the channel is simply called "AuthZAdminCh"
( despite hierarchical ordering under Microsoft-AzureMfa-AuthZ as presented in Event viewer )
The proven stanza is as simple as : [WinEventLog://AuthZAdminCh]