- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Extract fields in JSON during index time
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
I'm a newbie to splunk in field extractions. Appreciate any help on this.
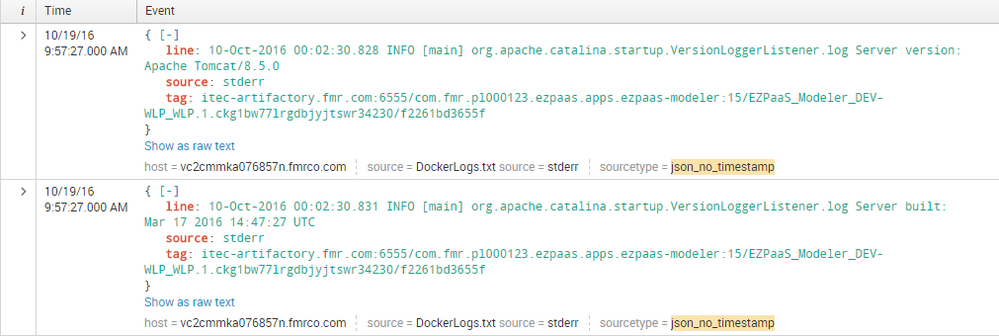
I have JSON Format logs like below:
I want source and tag as a field i.e it should not appear in events instead as separate fields like the way default fields appear on the left hand side in UI. Also I want the word "line:" to be removed. so basically only my line event should appear in splunk. How can I achieve this?
I believe props.conf and transforms should be a solution. But I dont know how to approach that. My transforms should contain a regex to capture what? I'm not understandin what my regex should do?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
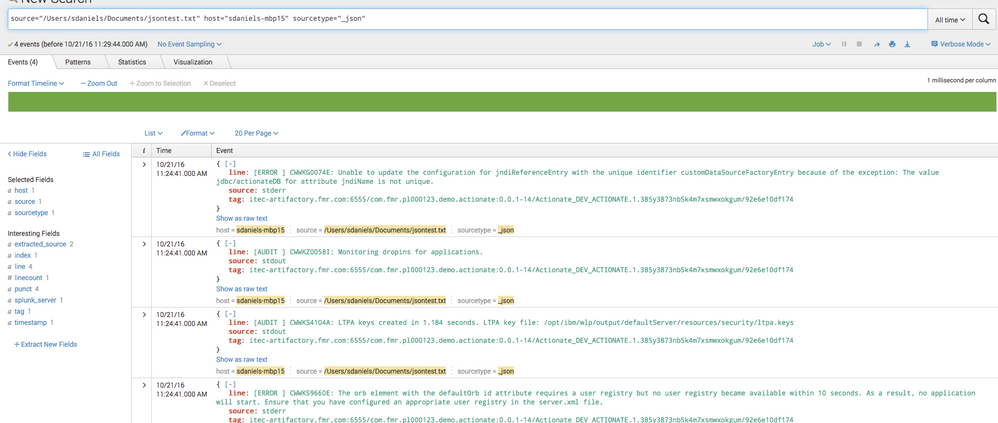
I don't believe you'll need any regex according to what i'm seeing. Or perhaps i don't understand exactly what you want to display. I am using the lastest Splunk 6.5 and this is what I get when i ingest your events and assign _json as the sourcetype. That is simply the raw event viewer.
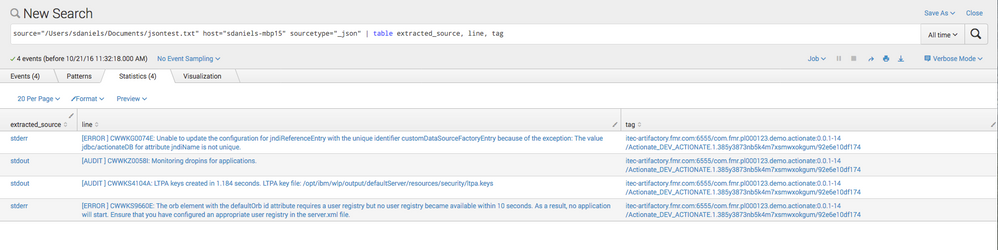
The fields are being created properly. Look at the left side in the above screenshot to see those extracted fields. Then, below then you can simply use the table command to display the data how you'd like to see it.