Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: How can I get multiple output in one cell and ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I get multiple output in one cell and upon clicking the output, it should show logs in a table below.
Below is the format.
statuscode for success =100, statuscode for warning = 200, statuscode for failure=300
| Country1 | Country2 | Country3 | |
| Application1 | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value |
| Application2 | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value |
| Application3 | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value | Success - #count_value Warning - #count_value Failure - #count_value |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This looks like it might be JSON? So, you field names might be something like this
| makeresults count=100
| eval _raw="{\"appName\":\"Application".(random()%3+1)."\",
\"countryCode\":\"Country".(random()%3+1)."\",
\"message\":{
\"countryCode\":\"Country".(random()%3+1)."\",
\"statusCode\":".100*(1+random()%3)."}
}
}"
| spath
| stats count by appName countryCode message.statusCode
| eval status=case('message.statusCode'==100,'message.statusCode'." - ".count,'message.statusCode'==200,'message.statusCode'." - ".count,'message.statusCode'==300,'message.statusCode'." - ".count)
| stats values(status) as status by appName countryCode
| eval status=mvjoin(status,"
")
| eval status=replace(status,"100 -","Success -")
| eval status=replace(status,"200 -","Warning -")
| eval status=replace(status,"300 -","Failure -")
| chart values(status) as status by appName countryCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults count=100
| eval app="Application".(random()%3+1)
| eval status=100*(1+random()%3)
| eval country="Country".(random()%3+1)
| stats count by app country status
``` the lines above set up some dummy data ```
| eval status=case(status==100,status." - ".count,status==200,status." - ".count,status==300,status." - ".count)
| stats values(status) as status by app country
| eval status=mvjoin(status,"
")
| eval status=replace(status,"100 -","Success -")
| eval status=replace(status,"200 -","Warning -")
| eval status=replace(status,"300 -","Failure -")
| chart values(status) as status by app country- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But sir,
If my country names are stored in a field_name as country and application_names are stored in a field_name as applicationName.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use your field names as appropriate then!
If you don't provide real example events etc., we have to make stuff up to demonstrate the solutions, and trust that you can understand the principles, so that you can implement for your specific case.
There are many different users out there and it is the principles which are important in the answers as they can be applied in multiple cases.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
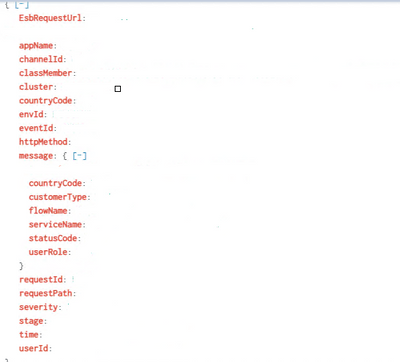
Fields in the logs are like this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This looks like it might be JSON? So, you field names might be something like this
| makeresults count=100
| eval _raw="{\"appName\":\"Application".(random()%3+1)."\",
\"countryCode\":\"Country".(random()%3+1)."\",
\"message\":{
\"countryCode\":\"Country".(random()%3+1)."\",
\"statusCode\":".100*(1+random()%3)."}
}
}"
| spath
| stats count by appName countryCode message.statusCode
| eval status=case('message.statusCode'==100,'message.statusCode'." - ".count,'message.statusCode'==200,'message.statusCode'." - ".count,'message.statusCode'==300,'message.statusCode'." - ".count)
| stats values(status) as status by appName countryCode
| eval status=mvjoin(status,"
")
| eval status=replace(status,"100 -","Success -")
| eval status=replace(status,"200 -","Warning -")
| eval status=replace(status,"300 -","Failure -")
| chart values(status) as status by appName countryCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sir , How to color the cell background as green, yellow and red according to failure percentage.
Only using splunk code. No external css should be used.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This sort of question has been asked and answered multiple times. Here is one answer
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Sir,
I want the colour of the cell according to Failure percentage, i.e. If Failure Percentage>90% then red, Failure percentage 50%-90% as yellow and Failure percentage as 0%-50% as green. Add the values are picked from the multiple value fields.
In the link you have provided, The coloumn name changes. Hence please provide a new solution.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to calculate the failure percentage and evaluate to given the colour you want and append that as the second multivalue
| makeresults count=100
| eval _raw="{\"appName\":\"Application".(random()%3+1)."\",
\"countryCode\":\"Country".(random()%3+1)."\",
\"message\":{
\"countryCode\":\"Country".(random()%3+1)."\",
\"statusCode\":".100*(1+(floor(log(random()%300))))."}
}
}"
| spath
| stats count by appName countryCode message.statusCode
| eventstats sum(count) as total by appName countryCode
| eval failures=if('message.statusCode'==300,100*count/total,null())
| eval status=case('message.statusCode'==100,'message.statusCode'." - ".count,'message.statusCode'==200,'message.statusCode'." - ".count,'message.statusCode'==300,'message.statusCode'." - ".count)
| stats values(status) as status values(failures) as failures by appName countryCode
| eval status=mvjoin(status,"
")
| eval status=replace(status,"100 -","Success -")
| eval status=replace(status,"200 -","Warning -")
| eval status=replace(status,"300 -","Failure -")
| eval failures=case(failures>90,"red",failures>50,"yellow",1==1,"green")
| eval status=mvappend(status,failures)
| chart values(status) as status by appName countryCode