- Splunk Answers
- :
- Using Splunk
- :
- Splunk Dev
- :
- Time-modifiers relative to the time-picker
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a Splunk query that returns 3 event types. I'd like the "Start" type events to be set by the time-picker and I'd like the "Stop" and "Portal" events to be driven by the time-picker plus or minus 2 days at each end. For example, if I choose the 2nd Aug for "Start" events I'd like to return the 1st to 3rd August for "Stop" and "Portal" events. Any ideas?
Thanks in advance.
index=50 (type="Start" AND termination_cause!="Resumed" {date range A})
OR (type="Stop" AND termination_cause!="Suspect-Logout" {date-range B})
OR (type="Portal" view="PortalView_Process_*" {date range C})
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
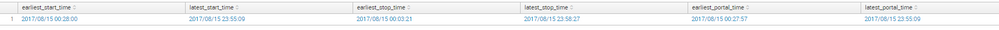
I've made some progress and I've now got the script to run (see below) but the output isn't what I was expecting. It appears that the time picker is overriding the time ranges set for the "Stop" and "Portal" events, so if I select yesterday (15th Aug) only events that occurred on the 15th for all three types are returned. I've also included a screenshot of the output. Any Ideas?
Thanks
index=50 (type="Start" AND termination_cause!="Resumed")
OR (type="Stop" AND termination_cause!="Suspect-Logout" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
OR (type="Portal" view="PortalView_Process_*" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
| eval session_start_time_unix=if(type="Start",_time,"")
| eval session_stop_time_unix=if(type="Stop",_time,"")
| eval session_portal_time_unix=if(type="Portal",_time,"")
| eval session_start_time=strftime(session_start_time_unix,"%Y/%m/%d %H:%M:%S")
| eval session_stop_time=strftime(session_stop_time_unix,"%Y/%m/%d %H:%M:%S")
| eval session_portal_time=strftime(session_portal_time_unix,"%Y/%m/%d %H:%M:%S")
| stats min(session_start_time) as earliest_start_time, max(session_start_time) as latest_start_time, min(session_stop_time) as earliest_stop_time, max(session_stop_time) as latest_stop_time, min(session_portal_time) as earliest_portal_time, max(session_portal_time) as latest_portal_time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've made some progress and I've now got the script to run (see below) but the output isn't what I was expecting. It appears that the time picker is overriding the time ranges set for the "Stop" and "Portal" events, so if I select yesterday (15th Aug) only events that occurred on the 15th for all three types are returned. I've also included a screenshot of the output. Any Ideas?
Thanks
index=50 (type="Start" AND termination_cause!="Resumed")
OR (type="Stop" AND termination_cause!="Suspect-Logout" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
OR (type="Portal" view="PortalView_Process_*" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
| eval session_start_time_unix=if(type="Start",_time,"")
| eval session_stop_time_unix=if(type="Stop",_time,"")
| eval session_portal_time_unix=if(type="Portal",_time,"")
| eval session_start_time=strftime(session_start_time_unix,"%Y/%m/%d %H:%M:%S")
| eval session_stop_time=strftime(session_stop_time_unix,"%Y/%m/%d %H:%M:%S")
| eval session_portal_time=strftime(session_portal_time_unix,"%Y/%m/%d %H:%M:%S")
| stats min(session_start_time) as earliest_start_time, max(session_start_time) as latest_start_time, min(session_stop_time) as earliest_stop_time, max(session_stop_time) as latest_stop_time, min(session_portal_time) as earliest_portal_time, max(session_portal_time) as latest_portal_time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just some kind off feedback - I tried a partial search taken from your current one:
index=syslogs [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""]
This works as expected. I tried as a normal search and also as a report.
BTW [OT]: could you tell me how to format code with line numbers?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this
*Updated (added format command to resolve search time error) *
index=50 (type="Start" AND termination_cause!="Resumed")
OR (type="Stop" AND termination_cause!="Suspect-Logout" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
OR (type="Portal" view="PortalView_Process_*" [| gentimes start=-1 | addinfo | eval earliest=relative_time(info_min_time,"-2d@d") | eval latest=relative_time(info_min_time,"+2d@d") | table earliest latest | format "" "" "" "" "" ""])
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this. I seem to be getting an error when I try and run this search it says:
Error in 'search' command: Unable to parse the search: 'AND' operator is missing a clause on the left hand side.
Am I missing something?
Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try the updated answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this, it now runs but the time picker is overriding the time ranges set for the "Stop" and "Portal" events, so if I select yesterday (15th Aug) only events that occurred on the 15th for all three types are returned (see my update below). Any ideas as I'm out of them now. Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe you are missing a quote so the syntax isn't correct? Are both ANDs coloured?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you familiar with simple xml editing? I believe you could set different time ranges (as tokens) depending on the time picker setting. These tokens you could use in your search in place of date-range B or C.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have looked at this but it won't work for my use case as I am passing the query to Splunk via the js stack from a third party application. Thanks