- Splunk Answers
- :
- Using Splunk
- :
- Splunk Dev
- :
- Re: Field Extraction is capturing too much
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'm not great with regex and I've been looking at lots of examples of how to only grab the first instance of a match but I can't make it work. Here is what I've got so far:
^ErrorMsg\:\s(?<Error_Code>.*)\s\((?<Error_Timestamp>\d+\/\d+\/\d+\s\d+\:\d+\s\w+)\)
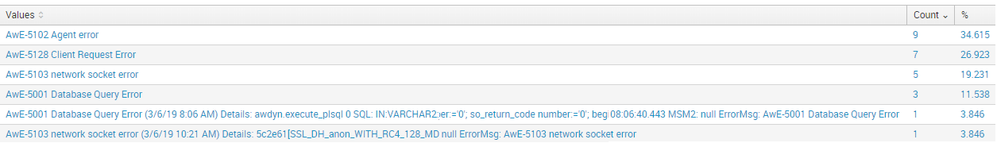
This returns the following:
You can see that the bottom two lines are going all the way out because they find a second match because of the way the event is being broken out for this source.
How can I get it to ONLY match the first instance of the error code and timestamp?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What nick says: fix your linebreaking, as it seems to be showing multiple events glued together.
But I would also try to avoid using .*. Assuming error codes cannot contain () characters, the following should also work and is much safer and also performs much better:
^ErrorMsg\:\s(?<Error_Code>[^\(]*)\s\((?<Error_Timestamp>\d+\/\d+\/\d+\s\d+\:\d+\s\w+)\)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want to trap only the first "AwE-4444 Agent/client/database/network" this could help
\w+-\d+\s\w+
Let me know if this helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for helping make it less greedy. Unfortunately, I don't know how many times I'd have to repeat the \s\w combo. I'm not sure how many words can be in the error code's name.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What nick says: fix your linebreaking, as it seems to be showing multiple events glued together.
But I would also try to avoid using .*. Assuming error codes cannot contain () characters, the following should also work and is much safer and also performs much better:
^ErrorMsg\:\s(?<Error_Code>[^\(]*)\s\((?<Error_Timestamp>\d+\/\d+\/\d+\s\d+\:\d+\s\w+)\)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with both you and Nick that the root of the issue is the sourcetype configuration but that one is beyond me. I'm hoping that our admin will be able to come up with something better.
Your suggestion worked perfectly though! TY
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The root cause of this looks like your event breaking is failing.
Have you configured any breaking or Timestamp extraction in props.conf for this sourcetype?