- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- stats not pulling through after a certain date
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
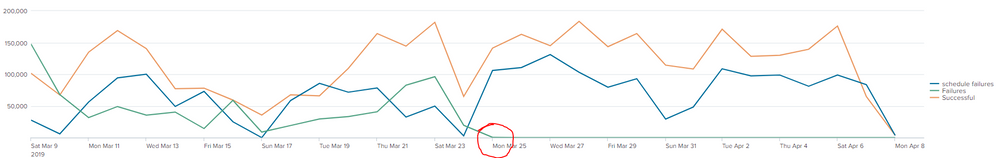
I have a search that looks at 2 indexes so it can pull 3 lots of separate data back so i can show data over a period of 30 days in a columns chart. This was working fine then all of a sudden the data stopped for one of the columns and i dont understand why. My search is as per the below:
(index=search1) OR (index=index2 someinfo) | eval errors=if(ErrorDescription="null",ErrorDescription, 1) | timechart count by errors span=1d | rename "-3600" as "schedule failures" | rename "0" as Failures | rename null as Successful
This brought through the below but as you can see the data went to 0 on the 25th March but the data still exists as i have searched the data for the that date and after and nothing has changed.
The only thing i can think of is that something has happened with the timechart config?
Any ideas appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ive changed my query round and got it working as the issue was to do with the multiple if statements i had and also how it worked with the multiple indexes. I changed it to the below and now working perfectly
(index=search1) OR (index=search2)
| eval errors=if(index="search2",1,if(ErrorDescription="null" AND index="search1", 2, 3))
| timechart span=1d count by errors | rename 1 as time_out, 2 as success, 3 as failure
I HAD to use quotations on the indexes aswell otherwise the answers were not correct for the eval but now gives me 3 columns with the data i need
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ive changed my query round and got it working as the issue was to do with the multiple if statements i had and also how it worked with the multiple indexes. I changed it to the below and now working perfectly
(index=search1) OR (index=search2)
| eval errors=if(index="search2",1,if(ErrorDescription="null" AND index="search1", 2, 3))
| timechart span=1d count by errors | rename 1 as time_out, 2 as success, 3 as failure
I HAD to use quotations on the indexes aswell otherwise the answers were not correct for the eval but now gives me 3 columns with the data i need
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You say that the data went to 0 on the 25th. Have you checked the statistics tab for the 25th and actually ascertained that the value in the count column is actually zero? It looks like a problem of the scale, your Y axis has large numbers. It is possible what looks like 0 in the visualisation is not zero but a relatively lower number. Please check your statistics tab out for the 25th
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From my investigation so far prior to the 25th it was splitting the data but now seems to be combining it into the schedule failures so when the failures disappeared it went into the schedule failures total but not sure why?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still outstanding if anyone can advise?