- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: "Value" Interesting Field - 2 different types ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello (again),
I have the following search:
index=perfmon host=(serverA OR host=serverB) (object="Processor" OR object="Memory" OR object="Network Interface")
The Interesting Fields that I need to utilize are:
cpu_percent
Value
The problem is that "Value" represents the memory percent and the network use in kb's
My question is - how do I write the search to break the 2 fields out as value for Memory and value for Network Usage?
Many thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the answer above, did not fully understood you.
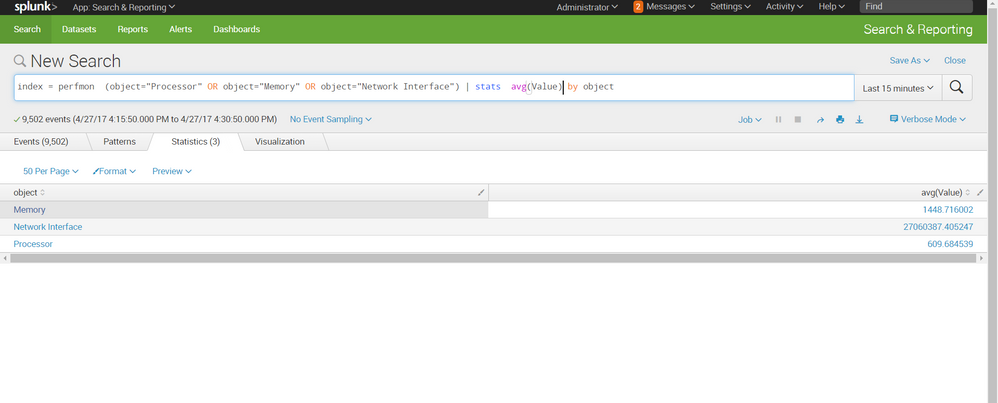
I think its not ideal to search by "object" as each object has more then one counter and each counter has values that match the counter so you can see for example under object="Processor" you have counters that represents percent (value between 0-100) and other that represents Interrupts/sec for example with values in range of 0-100000. that has large impact on the avg.
regardless, you can just split by whichever field you find valuable and splunk will obey:
index=perfmon host=(serverA OR host=serverB) (object="Processor" OR object="Memory" OR object="Network Interface") | stats avg(Value) by object cpu_percent field3 field4 fieldn
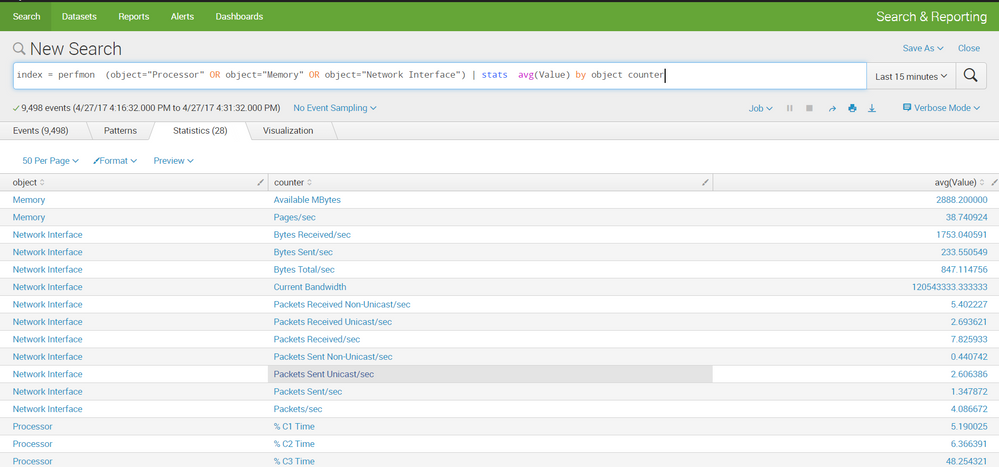
here are 2 screenshots, first is based on split by object, second is split by counter
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the answer above, did not fully understood you.
I think its not ideal to search by "object" as each object has more then one counter and each counter has values that match the counter so you can see for example under object="Processor" you have counters that represents percent (value between 0-100) and other that represents Interrupts/sec for example with values in range of 0-100000. that has large impact on the avg.
regardless, you can just split by whichever field you find valuable and splunk will obey:
index=perfmon host=(serverA OR host=serverB) (object="Processor" OR object="Memory" OR object="Network Interface") | stats avg(Value) by object cpu_percent field3 field4 fieldn
here are 2 screenshots, first is based on split by object, second is split by counter
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello there,
please check out this answer: https://answers.splunk.com/answers/522554/how-to-edit-my-alert-search-to-convert-available-m.html
the idea is that you can collect the right counter that shows percentage instead of trying to calculate based on 2 events with a common field name
there are other solution approaches within that answer as well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I don't think that this is what I am asking for help on.
I want to run this as one search and split out the Value field for Memory and the Value field for Network. No calculations involved.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
my bad, for misunderstanding the question.
another answer with screenshot in a second answer