- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Splunk query to check which user disabled/enab...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create a search to check which user disabled/enabled alert?
Splunk query to check which user disabled/enabled alert.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See what is in the logs like this:
index=_audit "disabled alert name here"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not sure @woodcock if the new version updated the audit log formats/my old 7.3 does not have yet your search query format,.. but i created a test alert and disabled and queried the audit index, but no match. something fishy.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have a report built in splunk that runs whenever any alert is disabled by a user in splunk. I want to find the user who has disabled the alert.Is this doable?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has this been answered... I am looking for the same thing as to WHO has done what?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @cmeisch
you can with following query
index="_internal" sourcetype="splunkd_ui_access" file IN (disable,enable)
i tried enable/disbale one of saved it , enable disable logs are showing with username who did that action
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the response. What I am trying to do is to see when a rule has been enabled\disabled and by who. I Your suggestion will give me who has disabled\enabled but I am trying to figure out what was enabled\disabled... BUT I am closer thanks to you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
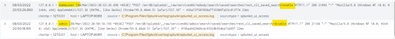
Hi @cmeisch
index="_internal" sourcetype="splunkd_ui_access" file IN (disable,enable)
| table _time user uri file
I am not good at regex😁, but hightlited the savedsearch name on which action done ,
after searches/ word is the report/alert name followed by action
---
If this reply helps you, an upvote/Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh my god finally, someone found it. Here is a revised query that works a little better and shows the "files" (searches) enabled by a particular user and decodes them to make them easier to read.
index="_internal" sourcetype=splunkd_ui_access method=POST
| eval file=urldecode(file)
| stats values(file) by user
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Care to elaborate?