- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- Is it possible to set up an alert that triggers wh...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to set up an alert that triggers when a value goes above a certain threshold?
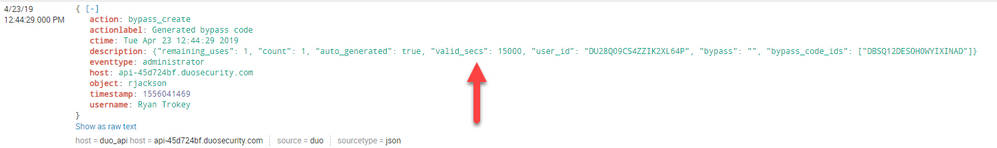
In the event that I want to set up an alert on, the value I want to check against is part of the description field. The description field is one long string with quite a few different pieces of information.
One of the pieces of information, and the one I am concerned about, is 'valid_secs'. This basically means how long this thing is valid.
Here is a screenshot of what I am trying to compare against.
Is it even possible to assign that value of 15000 to a variable, so that I can put something like the following into the search bar...
When 'valid_secs' is greater than 14000, send me an alert.
Does anyone know if this is even something I can manipulate with the current working tools of splunk?
I have been messing around with spath and field extraction and am having a tough time getting this to work.
Any suggestion or even a response saying you don't think this is possible is appreciated. Thank You!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just wanted to let everyone know how I figured this out.
The trick to getting this to work was using the FIELD EXTRACTOR and entering in my own custom REGULAR EXPRESSION.
JSON format can be tricky, it omits certain special characters. So I needed to view the event as "raw text" in order to see the extra backslashes that need to be accounted for.
The Regular Expression that I typed into the Field Extractor is below:
\\"valid_secs\\":\s(?\d+)
This Regular Expression was able to successfully extract the integer value that came after the words "valid_secs" and store it into its own field which I named 'valid_secs'.
Once this new field was extracted, I was able to type in the below search to get all events in which the field "valid_secs" was greater than the value 14400:
index=duo | search valid_secs>14400
I saved that search as an alert and I now get an alert every time that event is triggered.
Thank you to anyone who took the time to help and I hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use the extract fields to create a separate field for that if you see it reoccurring in multiple events.
https://docs.splunk.com/Documentation/Splunk/7.2.6/Knowledge/ExtractfieldsinteractivelywithIFX
After you get it extracted you can create an alert when that field is greater than your number.
Hope that helps.
Alspeedo