Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- I want to extract one field from different types o...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to extract one field from different types of events. Please let know how to extract "status" filed from below logs.
poojamande
New Member
08-03-2016
05:33 AM
Please find the below events. I want to extract the field which will have Error, Warning, info and error. Let me know how should I extract it , thanks
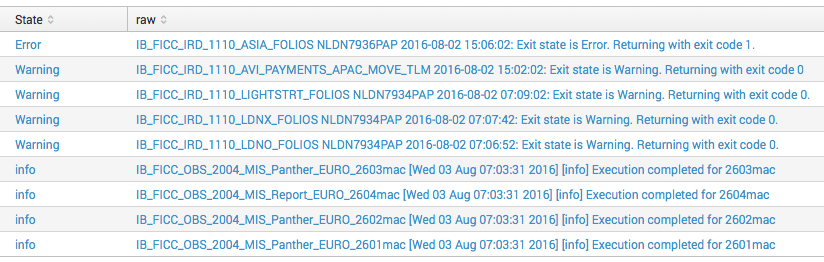
IB_FICC_IRD_1110_ASIA_FOLIOS NLDN7936PAP 2016-08-02 15:06:02: Exit state is Error. Returning with exit code 1.
IB_FICC_IRD_1110_AVI_PAYMENTS_APAC_MOVE_TLM 2016-08-02 15:02:02: Exit state is Warning. Returning with exit code 0
IB_FICC_IRD_1110_LIGHTSTRT_FOLIOS NLDN7934PAP 2016-08-02 07:09:02: Exit state is Warning. Returning with exit code 0.
IB_FICC_IRD_1110_LDNX_FOLIOS NLDN7934PAP 2016-08-02 07:07:42: Exit state is Warning. Returning with exit code 0.
IB_FICC_IRD_1110_LDNO_FOLIOS NLDN7934PAP 2016-08-02 07:06:52: Exit state is Warning. Returning with exit code 0.
IB_FICC_OBS_2004_MIS_Panther_EURO_2603mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2603mac
IB_FICC_OBS_2004_MIS_Report_EURO_2604mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2604mac
IB_FICC_OBS_2004_MIS_Panther_EURO_2602mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2602mac
IB_FICC_OBS_2004_MIS_Panther_EURO_2601mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2601mac
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
javiergn
Super Champion
08-03-2016
06:40 AM
Try this:
| rex field=YourField "(?msi)(Exit state is (?<State1>\w+)|\[(?<State2>\w+)\] Execution completed)"
| eval State = coalesce(State1, State2)
| fields - State1, State2
Example:
| stats count | fields - count
| eval _raw = "
IB_FICC_IRD_1110_ASIA_FOLIOS NLDN7936PAP 2016-08-02 15:06:02: Exit state is Error. Returning with exit code 1.
IB_FICC_IRD_1110_AVI_PAYMENTS_APAC_MOVE_TLM 2016-08-02 15:02:02: Exit state is Warning. Returning with exit code 0
IB_FICC_IRD_1110_LIGHTSTRT_FOLIOS NLDN7934PAP 2016-08-02 07:09:02: Exit state is Warning. Returning with exit code 0.
IB_FICC_IRD_1110_LDNX_FOLIOS NLDN7934PAP 2016-08-02 07:07:42: Exit state is Warning. Returning with exit code 0.
IB_FICC_IRD_1110_LDNO_FOLIOS NLDN7934PAP 2016-08-02 07:06:52: Exit state is Warning. Returning with exit code 0.
IB_FICC_OBS_2004_MIS_Panther_EURO_2603mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2603mac
IB_FICC_OBS_2004_MIS_Report_EURO_2604mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2604mac
IB_FICC_OBS_2004_MIS_Panther_EURO_2602mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2602mac
IB_FICC_OBS_2004_MIS_Panther_EURO_2601mac [Wed 03 Aug 07:03:31 2016] [info] Execution completed for 2601mac
"
| rex field=_raw max_match=0 "(?<raw>[^\n]+)"
| mvexpand raw
| fields - _raw
| rex field=raw "(?msi)(Exit state is (?<State1>\w+)|\[(?<State2>\w+)\] Execution completed)"
| eval State = coalesce(State1, State2)
| fields - State1, State2
Output: see picture below
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sundareshr
Legend
08-03-2016
06:33 AM
Try this regex in your props.
[<spec>]
EXTRACT-<class> = (?<status>[Ee]rror|Warning|[Ii]nfo)
Get Updates on the Splunk Community!
Updated Team Landing Page in Splunk Observability
We’re making some changes to the team landing page in Splunk Observability, based on your feedback. The ...
New! Splunk Observability Search Enhancements for Splunk APM Services/Traces and ...
Regardless of where you are in Splunk Observability, you can search for relevant APM targets including service ...
Webinar Recap | Revolutionizing IT Operations: The Transformative Power of AI and ML ...
The Transformative Power of AI and ML in Enhancing Observability
In the realm of IT operations, the ...