- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to pass argument (dynamically) to searchma...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to pass argument (dynamically) to searchmatch function without use map command
Hi,
I wonder test different pattern matching (format spl) dynamically with a field value without use the command "map"
example:
| makeresults | eval _raw = "foo var" | eval mymatch = "var OR fo*" | eval test = if(searchmatch($mymatch$),"yes","no")
I test with macro but it doesn't work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Argument for searchmatch is a string not a field. You need to put search string "var OR fo*" in searchmatch function.
| makeresults | eval _raw = "foo var" | eval test1 = if(searchmatch("var OR fo*"), "yes", "no"), test2 = if(searchmatch("var AND foo"), "yes", "no")
If you want to pass search string as a parameter then save your search as a saved search (Report) and use savedsearch command to call saved search with parameter:
<your search> | eval test = if(searchmatch("$search_string$"), "yes", "no")
Save this search as saved_search_name and call it using savedsearch command:
| savedsearch saved_search_name search_string="var OR fo*"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks!
But, your solution can't work with multiples patterns
My patterns are in a lookup, and for every patterns, i've specifics values in others fields.
The goal is to compare a lot of _raw with multiples patterns in my lookup for monitoring log.
does it exist a library in python for use function searchmatch ?, i can develop a custom command with it that will take parameter in searchmatch function because is not possible dynamically with splunk core without use map command.
my wish:
| makeresults | eval _raw="foo bar var"| eval different_pattern ="var OR test,foo AND bar,bar" | makemv different_pattern delim="," | mvexpand different_pattern_spl_format | eval result =if(searchmatch($different_pattern_spl_format_value$),"yes","no")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The goal is to compare a lot of _raw with multiples patterns in my lookup for monitoring log.
use lookup(wildcard)
https://answers.splunk.com/answers/52580/can-we-use-wildcard-characters-in-a-lookup-table.html
But why do you need to search the log itself?
it is better to extract like msg field and compare these.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
searchmatch(X) Use this function to return TRUE if the search string (X) matches the event.
reference:https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/CommonEvalFunctions
sample solution:
| makeresults | eval _raw="foo bar"
| eval test = if(searchmatch([|makeresults |eval query="\"bar\""|fields - _*]),"yes","no")
|appendpipe[
| eval test = if(searchmatch([|makeresults |eval query="\"foo\""|fields - _*]),"yes","no")
|appendpipe[
| eval test = if(searchmatch([|makeresults |eval query="\"foo OR bar\""|fields - _*]),"yes","no")]]
Sorry, I have a mistake.
Inside searchmatch, it can't use boolean expression like OR.
check my latest comment and try lookup(wildcard)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://answers.splunk.com/answers/52580/can-we-use-wildcard-characters-in-a-lookup-table.html
But why do you need to search the log itself?
it is better to extract like msg field and compare these
@to4kawa
Because in the lookup, the pattern is in splunk format with "OR" "NOT" "AND" (operator) not only wildcard like this "*"
i've the index, the sourcetype and the pattern in splunk format and others fields , i put a "join" in my spl on index and sourcetype for every eventlog and after i want test dynamically all patterns for fill every fields for ITSI app.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
foo.csv
sample
A OR b
*foo
bar
sample query:
index=yours [ | inputlookup foo.csv | table sample | return 1000 $sample]
you can do it like that.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@to4kawa
index=yours [ | inputlookup foo.csv | table sample | return 1000 $sample]
i already do that in the root search . But after in the same lookup , i've a description , severity, order, etc..
how i can connect the matches events with the spl pattern in the lookup for output the other fields without use map command ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=sample
| lookup foo.csv host OUTPUT description
| lookup foo.csv user OUTPUT severity
| lookup foo.csv bar OUTPUT baz
this is sample. lookup can use it again and again.
inputlookup is same.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@to4kawa
The ID is the pattern in SPL, it's for that i need a dynamically searchmatch that can indicate with what pattern spl the event _raw match for connect after with the lookup.
but i can't pass to the function searchmatch a field value.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see what you want. but I don't know the details ,logs , lookups.
I can't help and make SPL without these.
You don't provide these, so I think you'll write the SPL yourself.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@to4kawa
Thanks for the help! But it's doesn't work
Test the spl below:
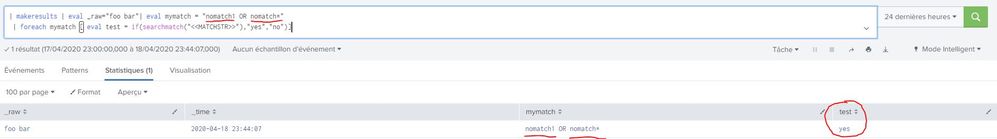
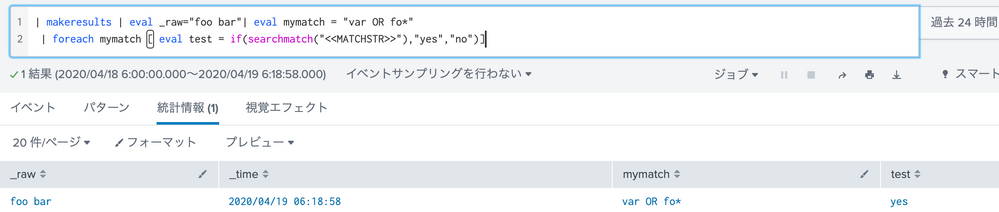
| makeresults | eval _raw="foo bar"| eval mymatch = "nomatch1 OR nomatch*"
| foreach mymatch [ eval test = if(searchmatch("<<MATCHSTR>>"),"yes","no")]
The result is too "yes", because it's blank. My version 7.3.0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it doesn't work, because it don't take the field value in the function searchmatch , it's a empty string.
In search.log:
04-18-2020 13:21:02.396 INFO ForeachProcessor - search for field 'mymatch' = eval test = if(searchmatch(""),"yes","no")