- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Why is my Splunk Cloud index filling up with spuri...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am currently evaluating Splunk Cloud for analyzing application logs which we are collecting in Azure Blob Storage.
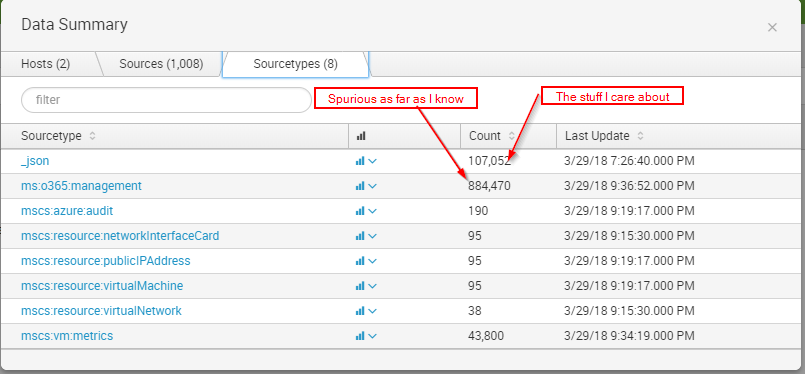
I have the Splunk Add-On for Microsoft Cloud Services installed. I currently have a single Storage Account configured, with a single Input using that account. I have not configured any Office 365, or any other account or connector. But I am seeing thousands and thousands of meaningless events of sourcetype="ms:o365:management":
Where are they coming from?
How can I stop them being indexed?
How can I delete them all once I have stopped them being collected?
Any help would be greatly appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It turns my trial Splunk Cloud instance included both Eventgen and Splunk Reference App - PAS, both of which are intended for app developers and were generating a very large number of events, which were of course no interest to me.
Thanks to both jconger and ragedsparrow for pointing me to the source of the events, which led me to figuring out how to disable those apps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It turns my trial Splunk Cloud instance included both Eventgen and Splunk Reference App - PAS, both of which are intended for app developers and were generating a very large number of events, which were of course no interest to me.
Thanks to both jconger and ragedsparrow for pointing me to the source of the events, which led me to figuring out how to disable those apps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the source of the data?
sourcetype="ms:o365:management" | stats count by source
This may give some indication on what input is generating the data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply. It appears the source is eventgen. Looking this up on Splunkbase makes me think this is for generating test data and is definitely something I do not need.
I will go and disable and/or delete it, if I can figure out how.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can go to the app location:
$SPLUNK_HOME/etc/apps/Splunk_TA_microsoft-cloudservices/default
Once you are there, delete eventgen.conf and restart Splunk.
That should take care of it. The caveat to that is that you will need to delete it again if you update the app later on.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I access that in Splunk Cloud?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be able to disable the Eventgen app under the Manage Apps section. On the upper left, you should see the Manage Apps listed in the Apps drop down. You should be able to disable the Eventgen app there.
You can also access it by going to:
/en-US/manager/launcher/apps/local
example: https://mysplunkinstance.com:8000/en-US/manager/launcher/apps/local
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perhaps a Heavy Forwarder is sending this data in to your Splunk Cloud environment. Click the Hosts tab to see which hosts are sending data, or use a search like below:
sourcetype=ms* | stats count by host sourcetype
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply. All of the ms* source types are coming from 127.0.0.1. I am not sure I know exactly what a "Heavy Fowarder" is (I am new to Splunk), but from context I don't think they would show as coming from the localhost, right?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will edit the original question to include this information.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, seems I can't edit my question any more. Oh well.