- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- SiLK Add-On using instrumentation app
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SiLK Add-On using instrumentation app
I have to use the SiLK Technology Add-On for a dataset for some testing on a single instance.
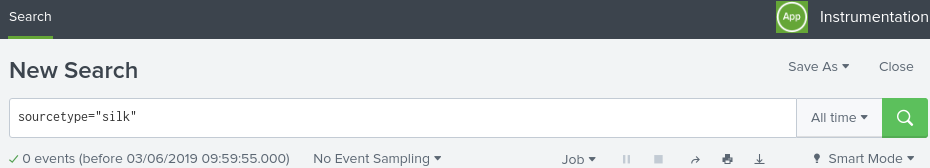
I have configured it and I can see under Data Inputs that the number of files and sourcetype (silk) get reocgnised correctly and the add-on is enabled, but 0 events appear in search. The sourcetype silk that was auto-configured by the SiLK add-on has a destination app of "Instrumentation" which cannot be changed. Even when selecting the Instrumentation app in settings and then doing a basic search, 0 events come up, as shown below:
I don't really understand what the Instrumentation app is. Does anyone have experience with it or with the SiLK Add-On and how to use it?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Convert the data to ascii. SILK provides a tool for doing that. Also Analysis-Pipeline should do it for you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Think you may have to convert the files to ascii. Just a guess. SiLK provides a tool enabling Wireshark and such to read flow captures.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using sourcetype="silk" index=*, I can now see events coming up but all content shows jibberish characters (binary files) and incorrect timestamps...