- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: Search Show result where count > 10
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Currently I use this search:
index=Linux | search host!="test*" | timechart span=1d count by HCS | timewrap 1w
To get the following result:
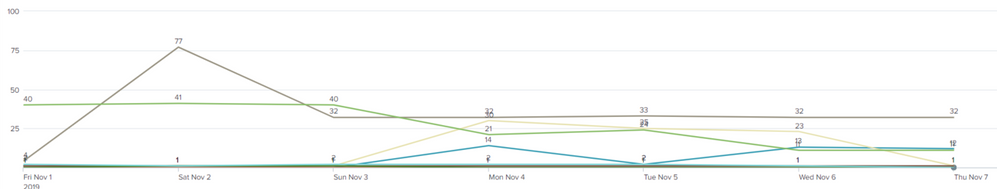
But as you can see, there are some results with 0 because of the count. I want to exclude everything that is zero.
I thought of something like this:
index=Linux | search host!="test*" | timechart span=1d count by HCS where count >= 1| timewrap 1w
But that doesn't seem to work.. What would be a correct way of excluding zero values?
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
try this
index=Linux | search host!="test*" |bin span=1d _time | stats count by HCS,_time|where count >10|timechart span=1d values(count) by HCS| timewrap 1w
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When removing Timewrap the zero results won't show, I just have to set the time with the date picker in the top right.
If I can't solve it otherwise, I'll use this as a solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
try this
index=Linux | search host!="test*" |bin span=1d _time | stats count by HCS,_time|where count >10|timechart span=1d values(count) by HCS| timewrap 1w
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I actually want to remove only the zero values, so >=1 should be ok. Should've stated in the title. But anyway, when using your search (With >=1 or >1) I get the same results, only the results that where higher than 1 previously are now all 1. So for example the 77 on november 2th is now 1.. Not sure why the results are being modified to 1?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sorry, pehaps I am not able to grasp.
You want a timechart of the values whose count is >0?
If yes, then you can just modify the timechart part of the query above to something like this:
previous stuff...|timechart span=1d values(count) by HCS|..rest of the stuff
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No problem, I indeed want the results to not show 0 so >=1 or >0 should work. When I show results with 0 the line chart and legend of the line chart get really cluttered with unusefull data. So that's my reason get rid of them.
You mean like this?:
index=Linux HCS "NOT OK" | search host!="test*" | bin span=1d _time | stats count by _time,HCS |timechart span=1d count by HCS where count > 1| timewrap 1w
Then all results are still 0 or 1. Results with more than 1 are changed to 1.. Not sure why?
Thanks for your assistance!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=Linux HCS "NOT OK" | search host!="psas*" host!="pccc*" host!="pisefibl*" host!="psapsap*" host=p* | bin span=1d _time | stats count by _time,HCS |timechart span=1d values(count) by HCS where count > 1
modified the timechart portion a bit to get the vlaues of the count. check first without timewrap and then with timewrap
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works indeed. Both with and without timewrap. But can you explain why _time and HCS is in count and in the next pipe, you count HCS again?
Thanks a lot!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The point is if you apply a straight timechart without the stats command, you will get an output with time as first column and the names of the HCS field from column 2 onwards.
Now, that is not what you needed. the key here are the bin and the stats commands.
the bin is used to split time into 1 day intervals. the stats counts the HCS values against the time split of 1 day each.
Remove all code after the stats and see the output, you will get 3 columns, _time, the field names for HCS and a third column 'count'.
Now , I simply take the values of the count, values(count) and apply a timechart.
The reason why my first code was just giving you 1 or 0 is because i was using timechart count, which was merely counting the count (occurences) of the stats command output and not the values of the count as you wanted.
I am sure if you see the output till the stats command after removing rest of the code , you will understand.
Please accept the answer if this resolves your issue 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jonydupre
Please check my answer in the below post.
https://answers.splunk.com/answers/667235/how-to-timechart-for-only-the-10-highest-counted-v.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The amount of results vary each day, so using top 10 would sometimes show less results than there actually are since I would only show top 10.. And in days where there are not so many results, it would also show the results with 0 and 1 if you know what I mean. Or did I miss something in the topic?