- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- REGEX only returning top-line of nmap results.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
REGEX only returning top-line of nmap results.
I have the app installed on my SearchHead (for the dashboards & Searches), and I deployed the app on two machines separated by subnet (windows-based); utilizing nmap.cmd.
I get results when I do:
index="asset_discovery" sourcetype="ping_scan"
however, I see that the field extraction for the dest_ip seems to only pull the top host value... in this case:
dest_ip (3)--
192.168.0.0
192.168.1.0
169.254.0.0
when I look at the raw nmap output, it does, indeed have a full scan result:
# Nmap 7.80 scan initiated Fri Nov 01 15:03:05 2019 as: "C:\\Program Files\\nmap\\nmap.exe" -oG - -v -R -sP -PE 192.168.0.0/24
# Ports scanned: TCP(0;) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 192.168.0.0() Status: Down
Host: 192.168.0.1() Status: Up
Host: 192.168.0.2 (web.server.example.com) Status: Up
Show all 258 lines
Looking at props.conf:
[source::nmap]
SHOULD_LINEMERGE = False
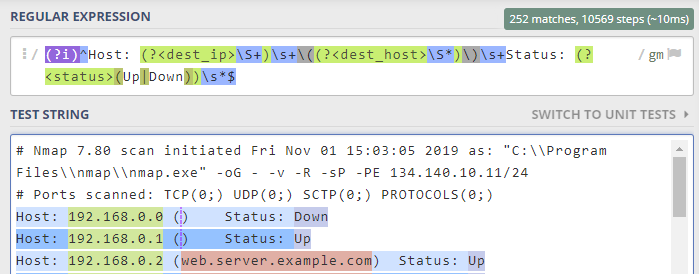
EXTRACT-nmap_ping = (?i)^Host: (?<dest_ip>\S+)\s+\((?<dest_host>\S*)\)\s+Status: (?<status>(Up|Down))\s*$
this checks out using my regex checker...
But for some reason, it's not picking up the other hosts from the nmap output.
Has anyone seen this before?
Second to this, I have not been able to get the port_scan to complete successfully on either of the scanning hosts.
Thanks, in advance.
--RP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@marycordova
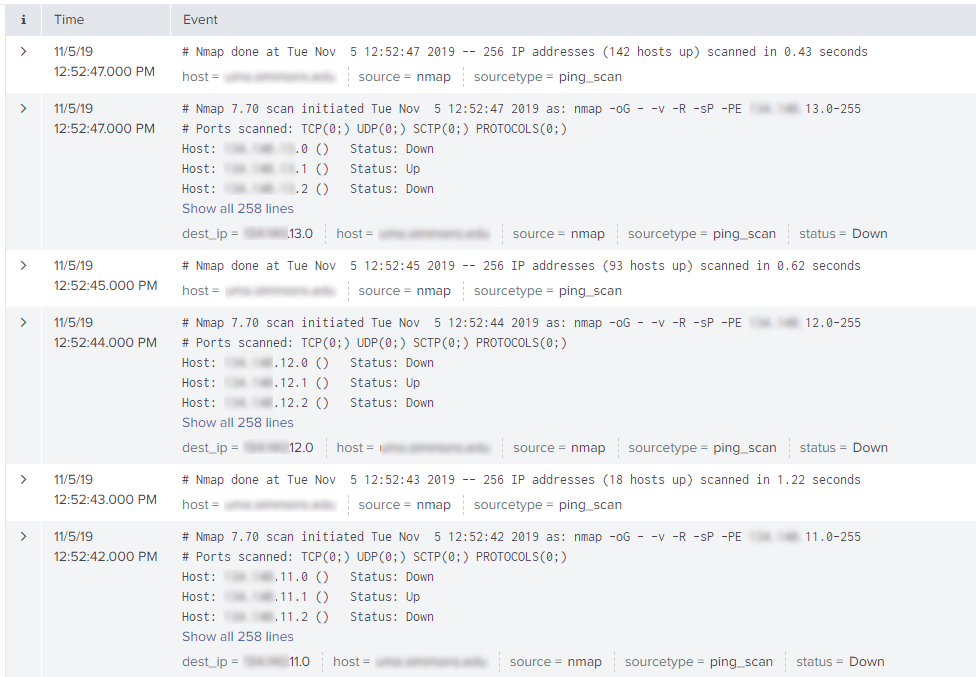
I don't believe the events are breaking correctly.
Please see the attached screenshot.
My props.conf:
# props.conf
[source::nmap]
SHOULD_LINEMERGE = False
EXTRACT-nmap_ping = (?i)^Host: (?<dest_ip>\S+)\s+\((?<dest_host>\S*)\)\s+Status: (?<status>(Up|Down))\s*$
[port_scan]
EXTRACT-nmap_full = (?i)^Host: (?<dest_ip>\S+)\s+\((?<dest_host>\S*)\)\s+Ports: (?<port_signature>.*?)(?:\s+Ignored Stat
e: \w+ \(\d*\))*(?:\s+OS:\s+(?<os_signature>.*?))*(?:\s+Seq Index:\s+(?<seq_index>\d+))*(?:\s+IP ID Seq: (?<ip_id>.*?))*
(?:\s+Status:\s+(?<status>(Up|Down)))*$
REPORT-nmap_portinfo = nmap_portinfo
FIELDALIAS-os = os_signature as os
FIELDALIAS-dest = dest_ip as dest
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
they look like they are breaking ok, can you expand one of the 258 line ones?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a copy of that event:
Nmap 7.70 scan initiated Tue Nov 5 13:28:51 2019 as: nmap -oG - -v -R -sP -PE 192.168.13.0-255
Ports scanned: TCP(0;) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 192.168.13.0 () Status: Down
Host: 192.168.13.1 () Status: Up
Host: 192.168.13.2 () Status: Down
[...]
Host: 192.168.13.232 () Status: Down
Host: 192.168.13.233 () Status: Down
Host: 192.168.13.234 () Status: Down
Host: 192.168.13.235 () Status: Down
Host: 192.168.13.236 () Status: Down
Host: 192.168.13.237 () Status: Down
Host: 192.168.13.238 () Status: Down
Host: 192.168.13.239 () Status: Down
Host: 192.168.13.240 () Status: Down
Host: 192.168.13.241 () Status: Down
Host: 192.168.13.242 () Status: Down
Host: 192.168.13.243 () Status: Down
Host: 192.168.13.244 () Status: Down
Host: 192.168.13.245 () Status: Down
Host: 192.168.13.246 () Status: Down
Host: 192.168.13.247 () Status: Down
Host: 192.168.13.248 () Status: Down
Host: 192.168.13.249 () Status: Down
Host: 192.168.13.250 () Status: Down
Host: 192.168.13.251 () Status: Down
Host: 192.168.13.252 () Status: Down
Host: 192.168.13.253 () Status: Down
Host: 192.168.13.254 () Status: Down
Host: 192.168.13.255 () Status: Down
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
try the change in the regex and see if that helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this regex Host:\s+(?<dest_ip>[\d\.]*)\s*\((?<dest_host>\S*)\)\s+Status:\s+(?<status>[Up|Down]+)
Additionally, a sample of the events from Splunk, not just the actual nmap output, would be helpful, I wonder if your event breaking is working correctly or not.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Query has a source type, but props.conf has a source. Is the source correct when searching with a query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
They all have source="nmap"