Join the Conversation
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- How to get Data into the app
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to get Data into the app
Hey i have installed this app. But I got one question: How do I get any Data from my big IP to this app? Is there any manual or something like that?
thx a lot
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It took some doing, but I finally got this working.
You DO NOT NEED Splunk_TA_f5-bigip.
First thing, make sure the F5 is sending Remote Storage -> Type = "Reporting Server"
You will need to set the sourcetype for the incoming date to asm_log. You can do this by dedicating a port to this input and setting sourcetype based on the port, or you can use a regex on the heavy forwarder.
This worked for me, YMMV: Note: sourcetype for my incoming was syslog
in props.conf (on heavy forwarder)
[syslog]
TRANSFORMS-sourcetype=f5-asm
in transforms.conf (on heavy forwarder)
[f5-asm]
DEST_KEY = MetaData:Sourcetype
REGEX =\w{3}\s\d{1,2}\s\d{2}\:\d{2}\:\d{2}\s\d+\.\d+\.\d+\.\d+\s\w{3}\s\d{1,2}\s\d{2}\:\d{2}\:\d{2}\s[^\s]+\sASM\:
FORMAT = sourcetype::asm_log
On the Search Head side
The default tokenizer is completely messed up, as noted here: https://answers.splunk.com/answers/189860
create a local/props.conf (search head)
[asm_log]
REPORT-10-asm_tokenizer = asm_tokenizer
And in the local/tranforms.conf
[asm_tokenizer]
# WOT?-> REGEX = ([^=,]+)=Ó(((\\.)|([^\\Ó]))+)Ó
REGEX = ([^=,\:]+)="([^\.]+)|([^\"]+)"
FORMAT = $1::$2
Note: there is an additional ':' in the first capture, this fixes the critical unit_hostname field, as noted here: https://answers.splunk.com/answers/121183
My index for the incoming data was 'f5' , so everything needed to be adjusted to use this index.
Create local/macros.conf:
[f5_get_indexes]
definition = index=f5
Now comes the fun part.
Every dashboard needs to have every query (including the dynamic queries in the inputs) changed to use the default index macro
In the source of every dashboard, find 'sourcetype=' and append
`f5_get_indexes`
( use backticks, this is a macro )
While you are in there, set default "all' for all the inputs and set the timepicker to something reasonable (defaults to "all time")
If anyone knows how I can put in a pull request for this, let me know.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the documentation for the Splunk Add-on for F5 BIG-IP:
http://docs.splunk.com/Documentation/AddOns/latest/F5BIGIP/Setup
Basically since you can't install a forwarder on the F5 device, you need to configure iRules on the F5 to send the data to Splunk.
Technically you can manually pull the F5 logs and feed them into Splunk as you would any other file, being sure to add them to the proper index, but it is a bit more time consuming and you don't get the live feed of events, just whatever was in that particular log at that time.
The process is pretty much the same for the various Splunk for F5 apps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I´ve done that...
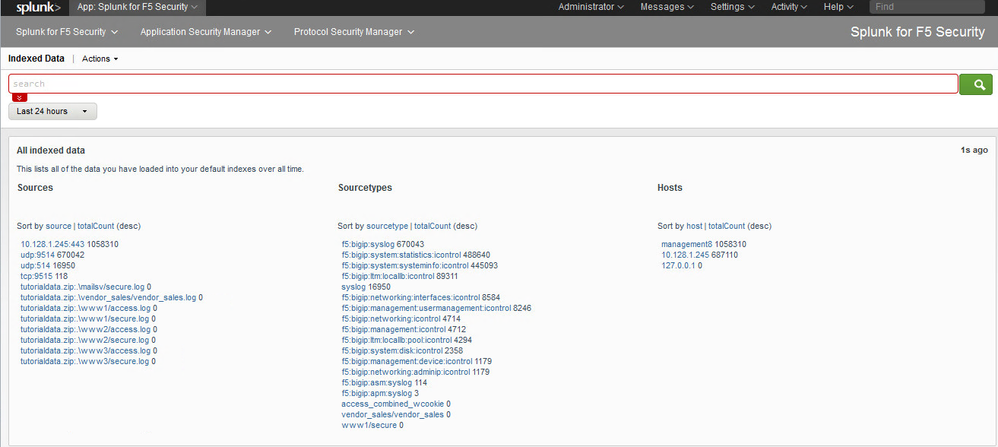
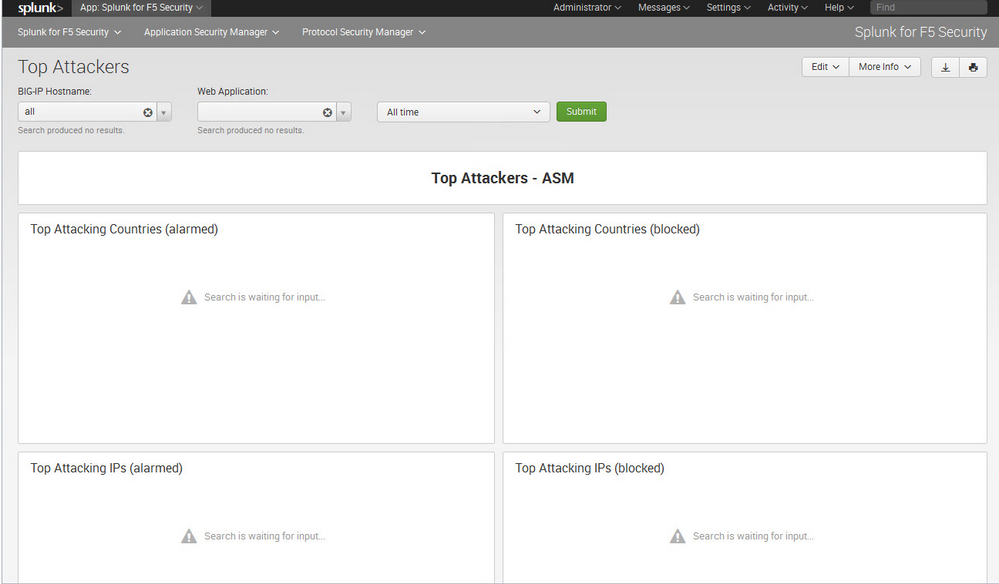
But my splunk app looks like that
The preconfigured Dashboard didn´t collect any data.
I use splunk 6.2 and the app is made for 6.0 might this be the problem?
thx
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pictures aren't showing up...