Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- FireEye Add-on for Splunk Enterprise: Why is some ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
We are getting FireEye logs in XML format over SYSLOG - TCP. I see some of the information is missing in the events in Splunk. Did anyone had this issue?
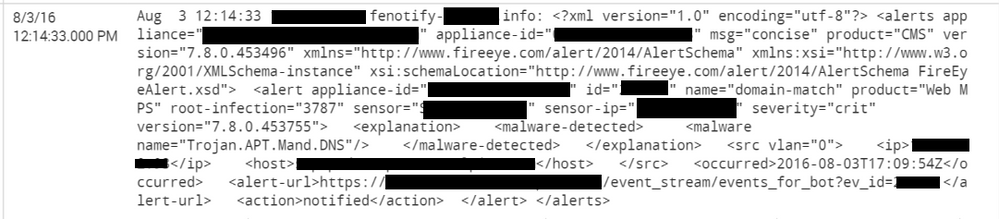
Event in splunk:
Actual alert;
alerts:
msg: extended
product: CMS
version: XXXXXXXXX
appliance:XXXXXXXX
appliance-id: XXXXXXX
alert (id:XXXXXX, name:domain-match):
product: Web MPS
appliance-id: XXXXXXX
severity: crit
root-infection: XXXXX
version: XXXXX
sensor-ip: 1XXXXX
sensor: XXXXXX
explanation:
protocol: udp
analysis: content
malware-detected:
malware (name:Trojan.APT.Mand.DNS):
stype: blacklist
sid: XXXXXX
cnc-services:
cnc-service:
protocol: udp
port: XX
address: ab.org
src:
vlan: 4
ip: XXXXXXX
host: XXXXXXXX
port: XXXXXX
mac: XXXXXXXX
dst:
mac: XXXXXXXXX
occurred: 2016-08-03 17:45:27+00
mode: tap
label: A1
interface (mode:tap, label:A1): pether3
alert-url: XXXXXXX
action: notified
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We figured out the issue and wanted to close the loop here. At this time, we still do not recommend sending events from the CM for a number of reasons. One of those reasons is loss of fidelity.
Please see our recommendation at the top of our details page on Splunkbase:
"Note: Send events from the LMS appliances -- not from the CM appliance"
Source: https://splunkbase.splunk.com/app/1845/#/details**
If this advice changes, we will update the details page and add CM as a category on the main analytics dashboard. I hope that helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We figured out the issue and wanted to close the loop here. At this time, we still do not recommend sending events from the CM for a number of reasons. One of those reasons is loss of fidelity.
Please see our recommendation at the top of our details page on Splunkbase:
"Note: Send events from the LMS appliances -- not from the CM appliance"
Source: https://splunkbase.splunk.com/app/1845/#/details**
If this advice changes, we will update the details page and add CM as a category on the main analytics dashboard. I hope that helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you say "some data from FireEye logs missing"... Are you referring to the Splunk app dashboards not displaying all of the data contained within the XML packet? Or are you referring to the fact that some data did not make it over to the Splunk app?
Can we narrow the issue down to one of the following?
Display vs. Data sent
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The data is not getting in to splunk
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you send me an email via Help -> Send Feedback within the Splunk app so we can troubleshoot and then post the answer back here? Thanks.