- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: Create theHive Alert: update needed, does not ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Create theHive Alert: update needed, does not work
Not sure if this works on Splunk 7.x. Documentation is poor. I cannot get it configured to send alerts.
When creating an alert, under actions, I am not seeing an action for this alert add-in.
Within the application description:
"Simply set your auth parameters in the Python script, tie in your URL, a field to use as a unique identifier for sourceRef, and any tags / severity / TLP you want!"
I found the python script, but I do not see where to enter "auth parameters"
Tie in your URL - where?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can anyone help me on this? I've tried using create_thehive_alert app and ta-thehive-ce app. but no luck, i'm not able to connect splunk with thehive. What are all the configurations needs to be done exactly?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
First sorry as my message is not a direct answer to the topic
We use a lot splunk with TheHive in my company, for that I have spent many hours to "improve" this "for our usage".
And I think everyone can pick some info from that work, it is published here :
https://github.com/swiip81/create_thehive_alert
One of the main fix I have tried to implement is to allow a 'transparent' conversion from splunk fields ( key=value ) to TheHive observables ( type=value*s* ) which is in my opinion the crucial thing to master.
Hope it will be useful
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is great.
Funny timing, I just spent this morning doing pretty much the same thing as you except I made the original splunk field a tag (tags = [key],)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@FloSwiip can you help me on this? I've tried using create_thehive_alert app and ta-thehive-ce app. but no luck i'm not able to connect splunk with thehive. What are all the configurations needs to be done exactly?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Karthick,
I don't personally use the ta-thehive-ce only the create_thehive_alert from my github link, still in prod.
Main page is providing all the details to do the setup.
It should allow you to make it work
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disclaimer: I am a complete noob, I just installed splunk a couple of days ago.
The code would go here:
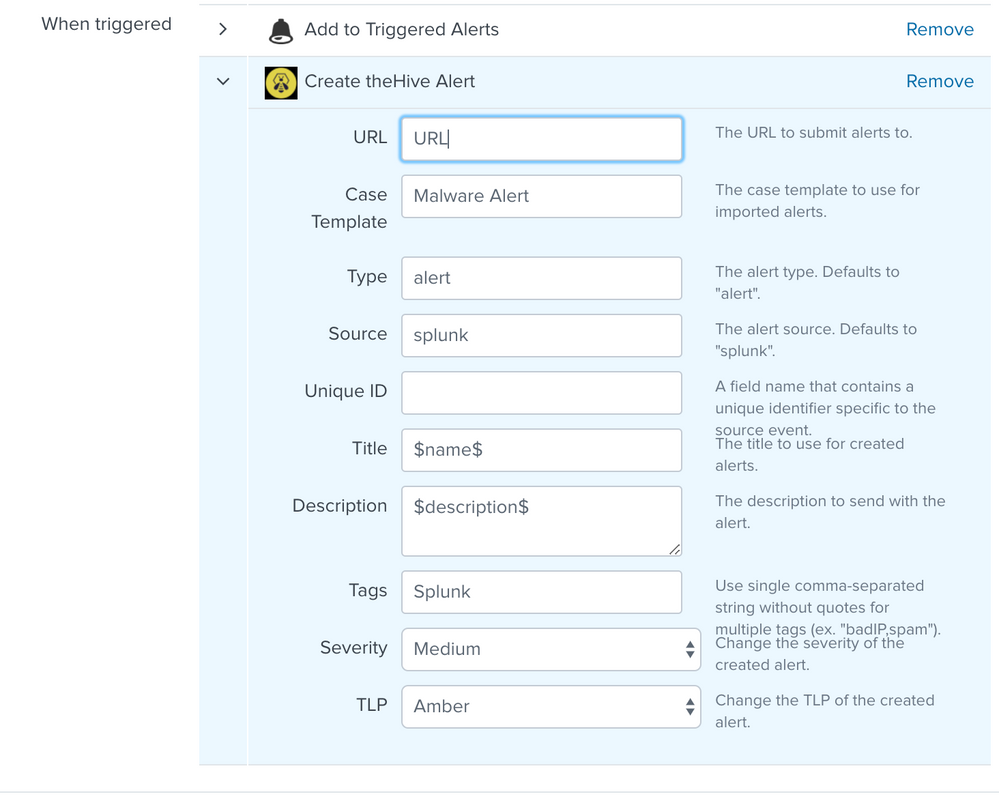
And you probably need to edit the permissions of alert to thehive app (under manage apps) to allow it to be visible to create alerts in other apps). I set mine to global.
Then you put the URL and other details under the alert:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, how do you call call the script (action). When creating alerts, you would typically click the Add Actions button, and pick the action from the "actions" the Hive action is not listed. There is an option to run a script, but there is a warning that this action is officially deprecated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Craig - thanks for the updated notes.
A few more questions:
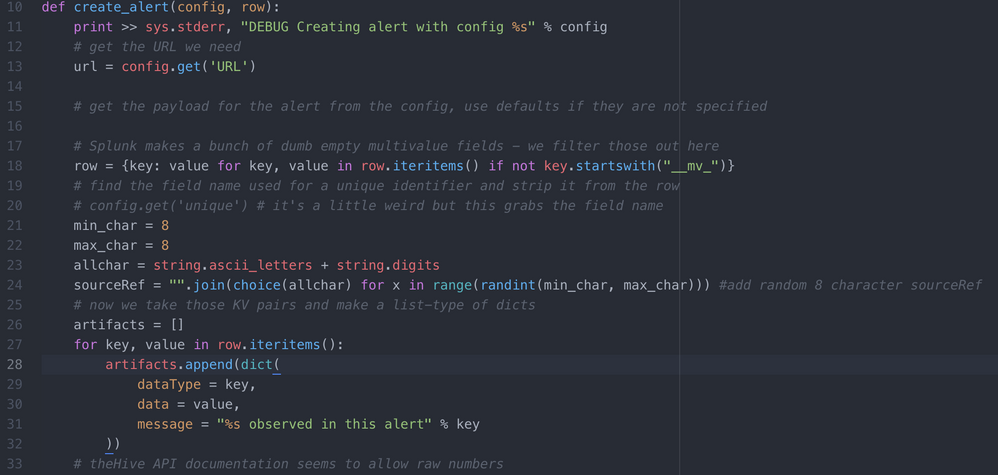
Where in the script does the URL of my hive instance go?
and where does all this go in the script:?
from random import *
min_char = 8
max_char = 8
allchar = string.ascii_letters + string.digits
sourceRef = "".join(choice(allchar) for x in range(randint(min_char, max_char))) #add random 8 character sourceRef
And commented out the "sourceRef = id"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I can see it goes in the alert trigger action in splunk
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I just set this up and got it working.
In the python script, the authentication username and password fields are in the line: response = requests.post(url, headers=headers, data=payload, auth=('username', 'password'), verify=False)
I also had to copy appIcon.png to thehive_logo_small.png under etc/apps/create_thehive_alert/appserver/static/ to fix the icon.
For my purposes, I did not have a good unique value for the sourceref. I then replaced that section of the python script.
I added imports for "random" and "string"
e.g. "import os, sys, json, gzip, csv, requests, random, string"
Then I added:
from random import *
min_char = 8
max_char = 8
allchar = string.ascii_letters + string.digits
sourceRef = "".join(choice(allchar) for x in range(randint(min_char, max_char))) #add random 8 character sourceRef
And commented out the "sourceRef = id"
I hope that helps
Cheers
Craig
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @mcbradfordwcb,
Thanks for posting. However, could you provide more info about this problem? Configuration settings, what exactly is the app not doing correctly, etc. Not only will that give you a greater chance of having your question answered, it will also help us categorize the issue so others with similar problems can learn from it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mcbradfordwcb
Yeah, I just checked out the page for that app on Splunkbase, and looks like it was last updated on July 24, 2017 last year to be compatible with version 6.6.x. It was created by a 3rd party developer, so hopefully they see this and can help you out. Looking at that page, it was built by someone named Miles Neff. I hope you get the guidance you need soon.
https://splunkbase.splunk.com/app/3642/