- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Cisco ASA: How to display a table with information...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cisco ASA VPN monitoring:
I haven't been able to finish this case for a week now. I need to display a table with information about start and end, and the total time of the user on the network.
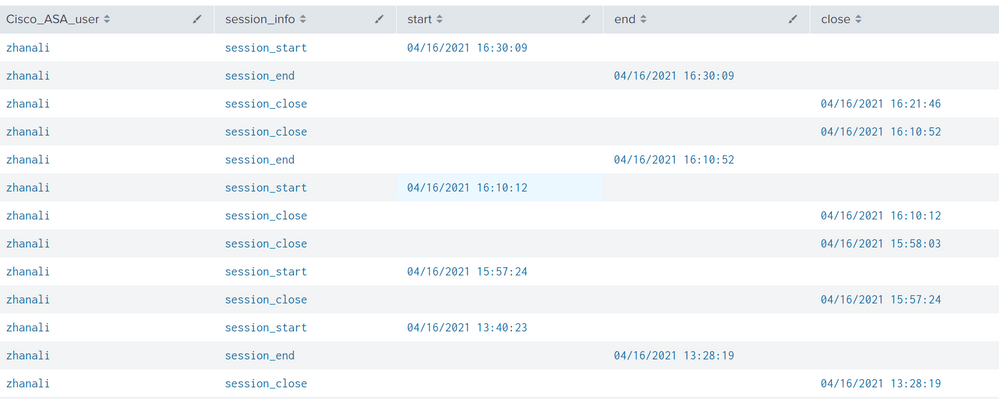
With the information that I collected and displayed in the table, it was like this:
sourcetype=cisco:asa message_id=722051 OR message_id=113019 OR message_id=722011 OR message_id=722037 OR message_id=722028 OR message_id=722010 zhanali
| eval session_info = case((message_id = "113019" OR message_id = "722011" OR message_id = "722010"), "session_end",message_id="722051", "session_start",message_id="722037" OR message_id = "722028","session_close")
| eval start = if((session_info = "session_start"),_time,"null")
| eval end = if((session_info = "session_end"),_time,"null")
| eval close = if((session_info = "session_close"),_time,"null")
| table Cisco_ASA_user session_info start end close
| convert ctime(start) ctime(end) ctime(close)
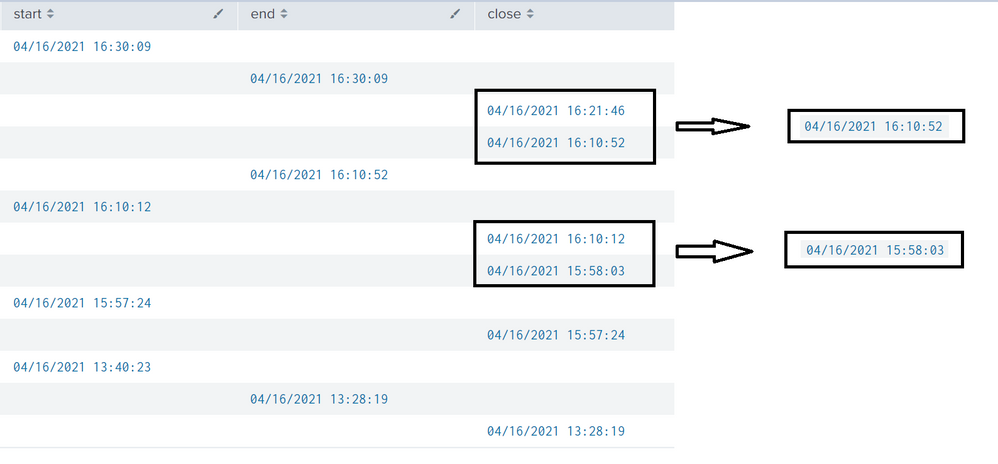
I need to somehow leave one line from the close lines that appear sequentially. Better to leave the first in time.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all! I forgot about this post. I decided with the simplest way, the start of the session is determined using the duration. Because I learned about the logs that the duration is sent when the session really was.
index="cisco_syslog" sourcetype="cisco:asa" message_id=113019
| eval start_time =_time-duration, end_time = _time
| sort -start_time
| table dvc group user src_ip start_time end_time duration
| eval duration = tostring(duration, "duration")
| convert timeformat="%H:%M:%S %d.%m.%Y" ctime(start_time) ctime(end_time)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all! I forgot about this post. I decided with the simplest way, the start of the session is determined using the duration. Because I learned about the logs that the duration is sent when the session really was.
index="cisco_syslog" sourcetype="cisco:asa" message_id=113019
| eval start_time =_time-duration, end_time = _time
| sort -start_time
| table dvc group user src_ip start_time end_time duration
| eval duration = tostring(duration, "duration")
| convert timeformat="%H:%M:%S %d.%m.%Y" ctime(start_time) ctime(end_time)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The events are currently separate events in the pipeline - is there anything in the data that can be used to correlate the events to determine if more than one close event is present? Or do you simply want to use _time to sequence the events?
sourcetype=cisco:asa message_id=722051 OR message_id=113019 OR message_id=722011 OR message_id=722037 OR message_id=722028 OR message_id=722010 zhanali
| eval session_info = case((message_id = "113019" OR message_id = "722011" OR message_id = "722010"), "session_end",message_id="722051", "session_start",message_id="722037" OR message_id = "722028","session_close")
| eval start = if((session_info = "session_start"),_time,"null")
| eval end = if((session_info = "session_end"),_time,"null")
| eval close = if((session_info = "session_close"),_time,"null")
| table Cisco_ASA_user session_info start end close
| sort _time
| streamstats values(session_info) as previous_session_info current=f window=2
| where previous_session_info != "session_close" OR session_info != "session_close"
| convert ctime(start) ctime(end) ctime(close)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Zhanali,
I am also building something similar. were you able to complete your syntax?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sourcetype=cisco:asa message_id=722051 OR message_id=113019 OR message_id=722011 OR message_id=722037 OR message_id=722028 OR message_id=722010 "MyUserName"
| eval session_info = case((message_id = "113019" OR message_id = "722011" OR message_id = "722010"), "session_end",message_id="722051", "session_start",(message_id="722037" OR message_id = "722028"),"session_close")
| eval start = if((session_info = "session_start"),_time,"null")
| eval end = if((session_info = "session_end"),_time,"null")
| eval close = if((session_info = "session_close"),_time,"null")
| sort - _time
| table _time Cisco_ASA_user session_info start end close duration
| eval duration = tostring(duration, "duration")
| convert ctime(start) ctime(end) ctime(close)
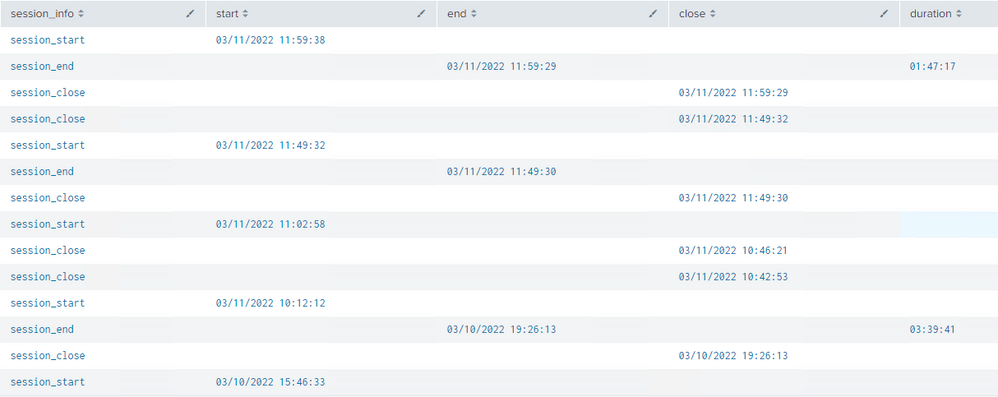
This issue was not resolved, but for this situation I found a way out.
If you look at the results of this query, it turns out that the event with duration field indicates a break of the session. This is what I used to calculate the session start time.