- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI
from the below query i will get calls count whose responseTime is morethan 10000 milliseconds
index="ab_cs" host="aw-lx0456.vint.ent" source="cb-ss-service"AND((RequestedURL ="/man/*/details" OR REQUESTED_URL="/man/*/contacts") OR (RequestedURL ="/contacts /*/details" OR REQUESTED_URL="/contacts/*/members"))AND (ResponseStatus OR HttpStatusCode)|sort -1 Timetaken | eval TimeTaken3=trim(replace(Timetaken, ",",""))| where TimeTaken3 >=10000 |stats count as ResponseOver10Sec
But here I want to send an alert when count of ResponseOver10Sec is more than 2% of total transaction
could you please suggest appropriate query??
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something like this should work
index="ab_cs" host="aw-lx0456.vint.ent" source="cb-ss-service"AND((RequestedURL ="/man/*/details" OR REQUESTED_URL="/man/*/contacts") OR (RequestedURL ="/contacts /*/details" OR REQUESTED_URL="/contacts/*/members"))AND (ResponseStatus OR HttpStatusCode)
| eval TimeTaken3=trim(replace(Timetaken, ",",""))
| stats count as Total sum(eval(if(TimeTaken3>=10000,1,0))) as ResponseOver10Sec
| where (ResponseOver10Sec/Total)>.02you don't need to use sort - that's just making your search slower.
If the responses over 10 seconds is > than 2% of the total of your urls searched for, then you will get a single result, otherwise you will get no results, so you can set up your alert accordingly
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something like this should work
index="ab_cs" host="aw-lx0456.vint.ent" source="cb-ss-service"AND((RequestedURL ="/man/*/details" OR REQUESTED_URL="/man/*/contacts") OR (RequestedURL ="/contacts /*/details" OR REQUESTED_URL="/contacts/*/members"))AND (ResponseStatus OR HttpStatusCode)
| eval TimeTaken3=trim(replace(Timetaken, ",",""))
| stats count as Total sum(eval(if(TimeTaken3>=10000,1,0))) as ResponseOver10Sec
| where (ResponseOver10Sec/Total)>.02you don't need to use sort - that's just making your search slower.
If the responses over 10 seconds is > than 2% of the total of your urls searched for, then you will get a single result, otherwise you will get no results, so you can set up your alert accordingly
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @bowesmana
Thanks and it worked.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
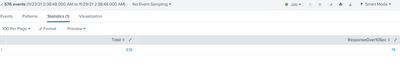
HI @bowesmana
I am getting response below
But i want to send an alert when this condition satisfies that means i need that count morethan 1