- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- How to join two search with event count?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to create an alert if any of the files are missing, a description printout for that. But this search only gives me one event although it should give me two. In a nutshell, the second part after append is not working. Individual search work. Please guide. It would be greatly appreciated.
index = axway abc@gmail.com *INCL* | stats count by host | where count = 0
| eval description="File1 INCL Missing"
|table description | append [search index = axway abc@gmail.com *POD* | stats count | where count = 0
| eval description="File2 POD Missing"
|table description]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I need to add another part before this search to make it work, but it works the way I want. Thanks for the response guys.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your search makes no sense, you cannot do
index = axway abc@gmail.com *INCL*
| stats count by host
| where count = 0 as this will always give you 0 results. Think about it - if you have 100 events for 2 hosts A and B then count by host will give you a count for hosts A and B. It can never give you a count for host C which has no data, so you can never get 0 for host C
If you are trying to find out if, for hosts A, B and C whether there is an event, then you need to have all your expected hosts in a lookup file and do something like
index = axway abc@gmail.com *INCL*
| stats count by host
| inputlookup append=t my_list_of_hosts
| stats values(count) as count by host
| fillnull count value=0
| where count = 0
| eval description="File1 INCL Missing"
| table description this will prove the negative for the first check. Then you can do this for the second one - but you could also combine this to a single search if the hosts are the same.
Hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
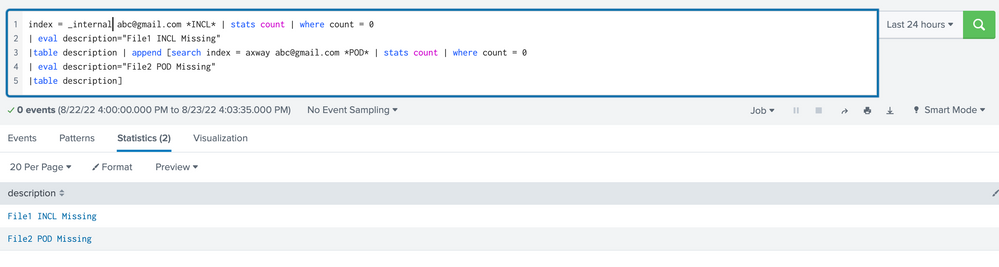
index = axway abc@gmail.com *INCL* | stats count | where count = 0
| eval description="File1 INCL Missing"
|table description | append [search index = axway abc@gmail.com *POD* | stats count | where count = 0
| eval description="File2 POD Missing"
|table description]Very much appreciate your reply. It should not be counted by the host. I apologize for that. Above is the search I am trying to search. All I am trying to do is combine search to alert us if any of the POD and INCL file is missing, and print the description for that search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Odd, it should work. If you run this
index = axway abc@gmail.com *INCL*
| stats count
| eval description="File1 INCL Missing"
| append [
search index = axway abc@gmail.com *POD*
| stats count
| eval description="File2 POD Missing"
]does it show you both rows with the count of results for each?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Above search should be working. Is it not working for you?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Individual search work, but not combined. When I combined only the first one of the event pops up(first part of search), not the second.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is working for me as is (Splunk v8.2.4)