- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- Combine two events which has unique field and get ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Combine two events which has unique field and get difference between those two events
Hi All, I haven3 events in splunk where there is one unique field in all the three events.
Here is the example:
[2022-05-10 23:17:23,049] [INFO ] [] [c.c.n.t.e.i.T.JmsMessageEventData] [] - channel="NPP_MPIR.CHANNEL", productVersion="1.3.1-0-1-404089bc7", uuid="3c78031b-12b3-4694-ab88-3a265bf8499e", eventDateTime="2022-05-10T23:17:23.049Z", severity="INFO", code="JmsMessageEventData", component="mq.listener", category="default", serviceName="Mandated Payment Initiation", eventName="MANDATED_PAYMENT_INITIATION.SERVICE_START", message="Mandated Payment Initiation Event", entityType="MSG", start="1652188643002", messageIdentification="CTBAAUSNXXX20220510020220510131721", queueManagerName="PGT201", queueManagerHostname="10.39.9.38",
Initial: [2022-05-10 23:17:24,425] [INFO ] [] [c.c.n.t.e.i.T.JmsMessageEventData] [] - eventDateTime="2022-05-10T23:17:24.425Z", severity="INFO", code="JmsMessageEventData", component="submission.sent", category="default", serviceName="Submission Service", eventName="PAYMENT_STATUS_REPORT.SENT", message="Customer initial status report sent to PAG", entityType="INSTR", externalSystem="PAG", start="1652188644418", stop="1652188644425", elapsed="7", exceptionInfo="null", messageIdentification="CTBAAUSNXXX20220510020220510131721", firstMessageTraceIdentification="2TDyn8AlRMud1mfUA49o6A"
These are the 3 events with unique field "messageIdentification", I need to combine 1 and 2 events and also 1 and 3 and get difference of time between them and calculate how much percentage of events are triggering in less than 15 sec and 30 sec.
|
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
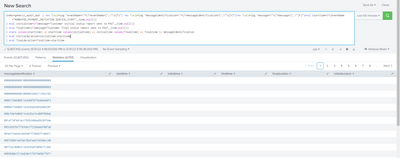
You need to go back a step - do you have a field called log? If not, you could do your rex against the _raw field (which is the default if no field is specified)
| rex "eventName=...- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Whisper,
Yes,i have log in my event and now am able to fetch events.and calculate time as well. But not able to calculate the initial percentage and final percentage as well. Can you please help me on the same.
Thanks in Advance.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you currently have? Please share the code in a code block </>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remove "stats count by eventName" - this is limiting the events to just two fields (count and eventName)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
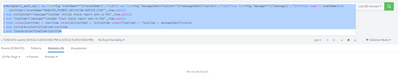
You can do a single huge ugly stats with evals but it's prettier to go with a solution similar to what @ITWhisperer 's started with. More or less something like this (assuming that you have one value per "type" of event):
<<your search>>
| eval starttime=if(eventName="MANDATED_PAYMENT_INITIATION.SERVICE_START",_time,null())
| eval initialtime=if(message="Customer initial status report sent to PAG",_time,null())
| eval finaltime=if(message="Customer final status report sent to PAG",_time,null())
| stats values(starttime) as starttime values(initialtime) as initialtime values(finaltime) as finaltime by messageIdentification
| eval initialduration=initialtime-starttime
| eval finalduration=finaltime-starttime
This way you have your duration times and can do aggregate summaries like counting and calculating percentages and so on.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming the fields have already been extracted
| eval eventStart=if(eventName="MANDATED_PAYMENT_INITIATION.SERVICE_START",_time,null())
| eventstats values(eventStart) as eventStart by messageIdentification
| eval initialTimeDiff=if(message="Customer initial status report sent to PAG", _time-eventStart, null())
| eval finalTimeDiff=if(message="Customer final status report sent to PAG", _time-eventStart, null())
| stats values(initialTimeDiff) as initialTimeDiff values(finalTimeDiff) as finalTimeDiff by messageIdentificationThis will get you the time differences - I am not sure what you are looking in terms of percentages and the two boundaries - for example, do you mean percentage of initial differences less than 15 and percentage of final differences less than 30 or percentages of both being less than 15 and both being less than 30?